By: W12-3 Since: AUG 2018 Licence: MIT
- 1. Setting up
- 2. Design
- 3. Implementation
- 4. Documentation
- 5. Testing
- 6. Dev Ops
- Appendix A: Text Prediction low level details
- Appendix B: Suggested Programming Tasks to Get Started
- Appendix C: Product Scope
- Appendix D: User Stories
- Appendix E: Use Cases
- Appendix F: Non Functional Requirements
- Appendix G: Glossary
- Appendix H: Instructions for Manual Testing
- H.1. Adding a person
- H.2. Editing a person
- H.3. Listing persons
- H.4. Selecting persons
- H.5. Predicting text
- H.6. Searching for a person
- H.7. Locking and unlocking
- H.8. Deleting a person
- H.9. Updating the Schedule
- H.10. Backing up and restoring data in the address book
- H.11. Exporting data from the address book
- H.12. Importing data to the address book
1. Setting up
1.1. Prerequisites
-
JDK
9or laterJDK 10on Windows will fail to run tests in headless mode due to a JavaFX bug. Windows developers are highly recommended to use JDK9. -
IntelliJ IDE
IntelliJ by default has Gradle and JavaFx plugins installed.
Do not disable them. If you have disabled them, go toFile>Settings>Pluginsto re-enable them.
1.2. Setting up the project in your computer
-
Fork this repo, and clone the fork to your computer
-
Open IntelliJ (if you are not in the welcome screen, click
File>Close Projectto close the existing project dialog first) -
Set up the correct JDK version for Gradle
-
Click
Configure>Project Defaults>Project Structure -
Click
New…and find the directory of the JDK
-
-
Click
Import Project -
Locate the
build.gradlefile and select it. ClickOK -
Click
Open as Project -
Click
OKto accept the default settings -
Open a console and run the command
gradlew processResources(Mac/Linux:./gradlew processResources). It should finish with theBUILD SUCCESSFULmessage.
This will generate all resources required by the application and tests.
1.3. Verifying the setup
-
Run the
seedu.address.MainAppand try a few commands -
Run the tests to ensure they all pass.
1.4. Configurations to do before writing code
1.4.1. Configuring the coding style
This project follows oss-generic coding standards. IntelliJ’s default style is mostly compliant with ours but it uses a different import order from ours. To rectify,
-
Go to
File>Settings…(Windows/Linux), orIntelliJ IDEA>Preferences…(macOS) -
Select
Editor>Code Style>Java -
Click on the
Importstab to set the order-
For
Class count to use import with '*'andNames count to use static import with '*': Set to999to prevent IntelliJ from contracting the import statements -
For
Import Layout: The order isimport static all other imports,import java.*,import javax.*,import org.*,import com.*,import all other imports. Add a<blank line>between eachimport
-
Optionally, you can follow the UsingCheckstyle.adoc document to configure Intellij to check style-compliance as you write code.
1.4.2. Updating documentation to match your fork
After forking the repo, the documentation will still have the SE-EDU branding and refer to the se-edu/addressbook-level4 repo.
If you plan to develop this fork as a separate product (i.e. instead of contributing to se-edu/addressbook-level4), you should do the following:
-
Configure the site-wide documentation settings in
build.gradle, such as thesite-name, to suit your own project. -
Replace the URL in the attribute
repoURLinDeveloperGuide.adocandUserGuide.adocwith the URL of your fork.
1.4.3. Setting up CI
Set up Travis to perform Continuous Integration (CI) for your fork. See UsingTravis.adoc to learn how to set it up.
After setting up Travis, you can optionally set up coverage reporting for your team fork (see UsingCoveralls.adoc).
| Coverage reporting could be useful for a team repository that hosts the final version but it is not that useful for your personal fork. |
Optionally, you can set up AppVeyor as a second CI (see UsingAppVeyor.adoc).
| Having both Travis and AppVeyor ensures your App works on both Unix-based platforms and Windows-based platforms (Travis is Unix-based and AppVeyor is Windows-based) |
1.4.4. Getting started with coding
When you are ready to start coding,
-
Get some sense of the overall design by reading Section 2.1, “Architecture”.
-
Take a look at Appendix B, Suggested Programming Tasks to Get Started.
2. Design
2.1. Architecture
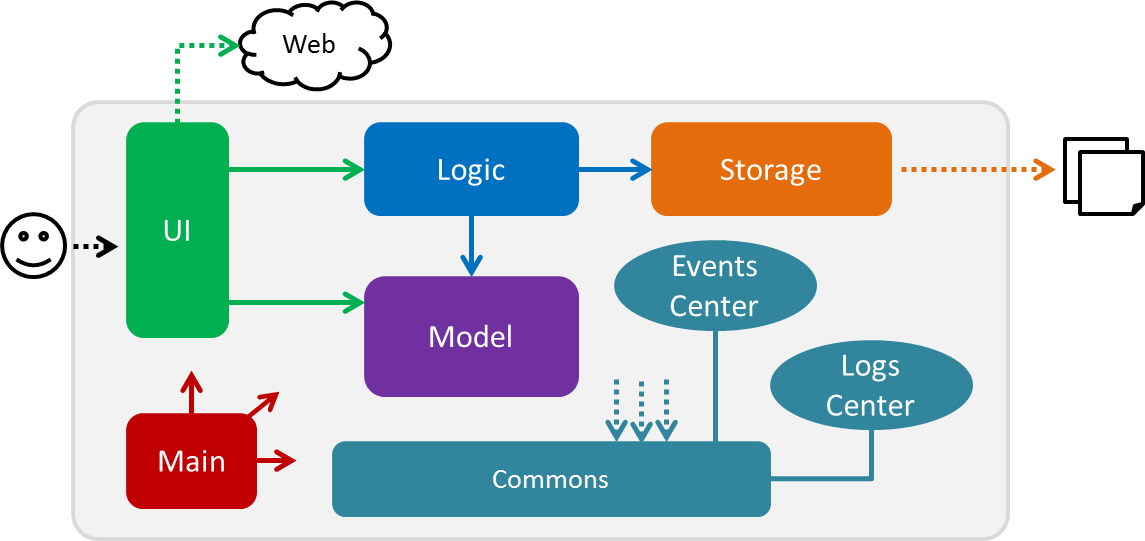
The Architecture Diagram given above explains the high-level design of the App. Given below is a quick overview of each component.
The .pptx files used to create diagrams in this document can be found in the diagrams folder. To update a diagram, modify the diagram in the pptx file, select the objects of the diagram, and choose Save as picture.
|
Main has only one class called MainApp. It is responsible for,
-
At app launch: Initializes the components in the correct sequence, and connects them up with each other.
-
At shut down: Shuts down the components and invokes cleanup method where necessary.
Commons represents a collection of classes used by multiple other components. Two of those classes play important roles at the architecture level.
-
EventsCenter: This class (written using Google’s Event Bus library) is used by components to communicate with other components using events (i.e. a form of Event Driven design) -
LogsCenter: Used by many classes to write log messages to the App’s log file.
The rest of the App consists of four components.
Each of the four components
-
Defines its API in an
interfacewith the same name as the Component. -
Exposes its functionality using a
{Component Name}Managerclass.
For example, the Logic component (see the class diagram given below) defines it’s API in the Logic.java interface and exposes its functionality using the LogicManager.java class.
Events-Driven nature of the design
The Sequence Diagram below shows how the components interact for the scenario where the user issues the command delete 1.
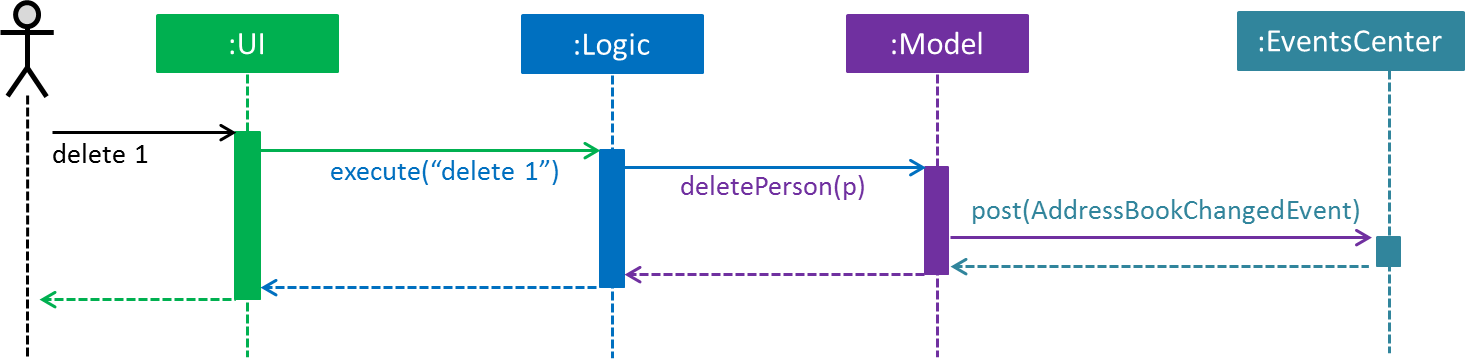
delete 1 command (part 1)
Note how the Model simply raises a AddressBookChangedEvent when the Address Book data are changed, instead of asking the Storage to save the updates to the hard disk.
|
The diagram below shows how the EventsCenter reacts to that event, which eventually results in the updates being saved to the hard disk and the status bar of the UI being updated to reflect the 'Last Updated' time.
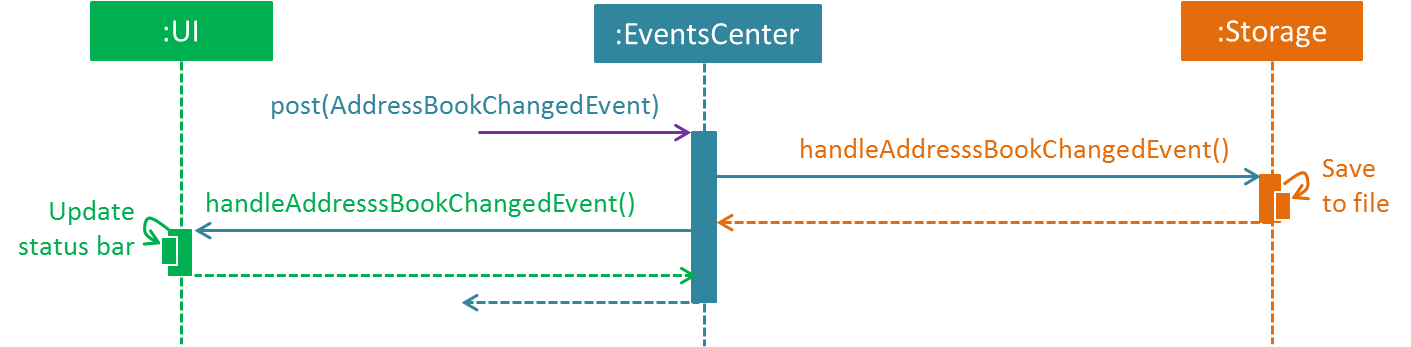
delete 1 command (part 2)
Note how the event is propagated through the EventsCenter to the Storage and UI without Model having to be coupled to either of them. This is an example of how this Event Driven approach helps us reduce direct coupling between components.
|
The sections below give more details of each component.
2.2. UI component
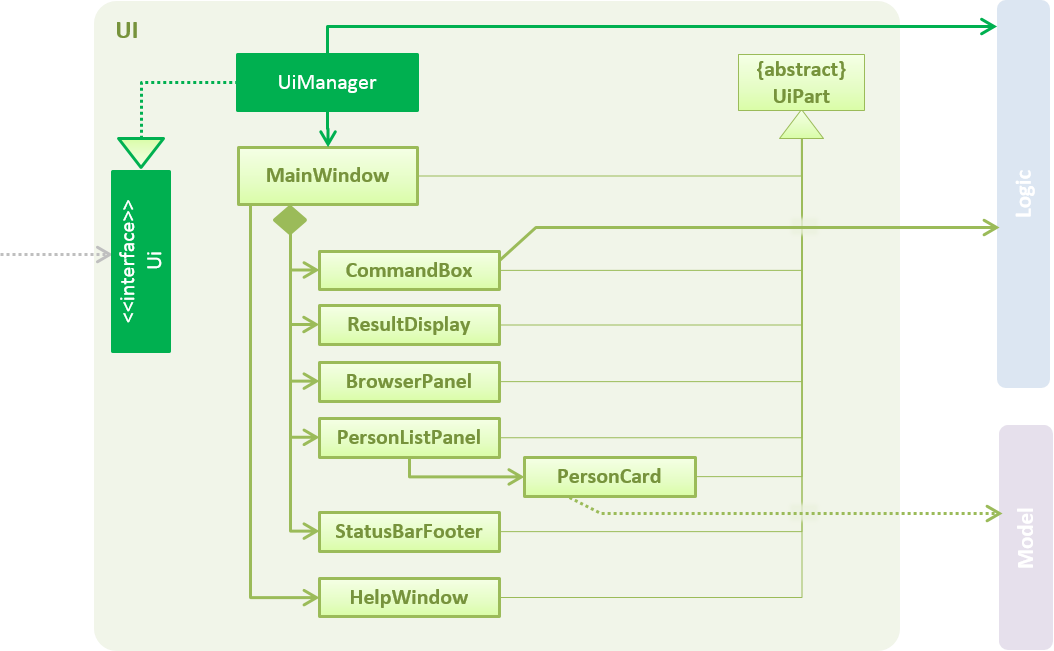
API : Ui.java
The UI consists of a MainWindow that is made up of parts e.g.CommandBox, ResultDisplay, PersonListPanel, StatusBarFooter, BrowserPanel etc. All these, including the MainWindow, inherit from the abstract UiPart class.
The UI component uses JavaFx UI framework. The layout of these UI parts are defined in matching .fxml files that are in the src/main/resources/view folder. For example, the layout of the MainWindow is specified in MainWindow.fxml
The UI component,
-
Executes user commands using the
Logiccomponent. -
Binds itself to some data in the
Modelso that the UI can auto-update when data in theModelchange. -
Responds to events raised from various parts of the App and updates the UI accordingly.
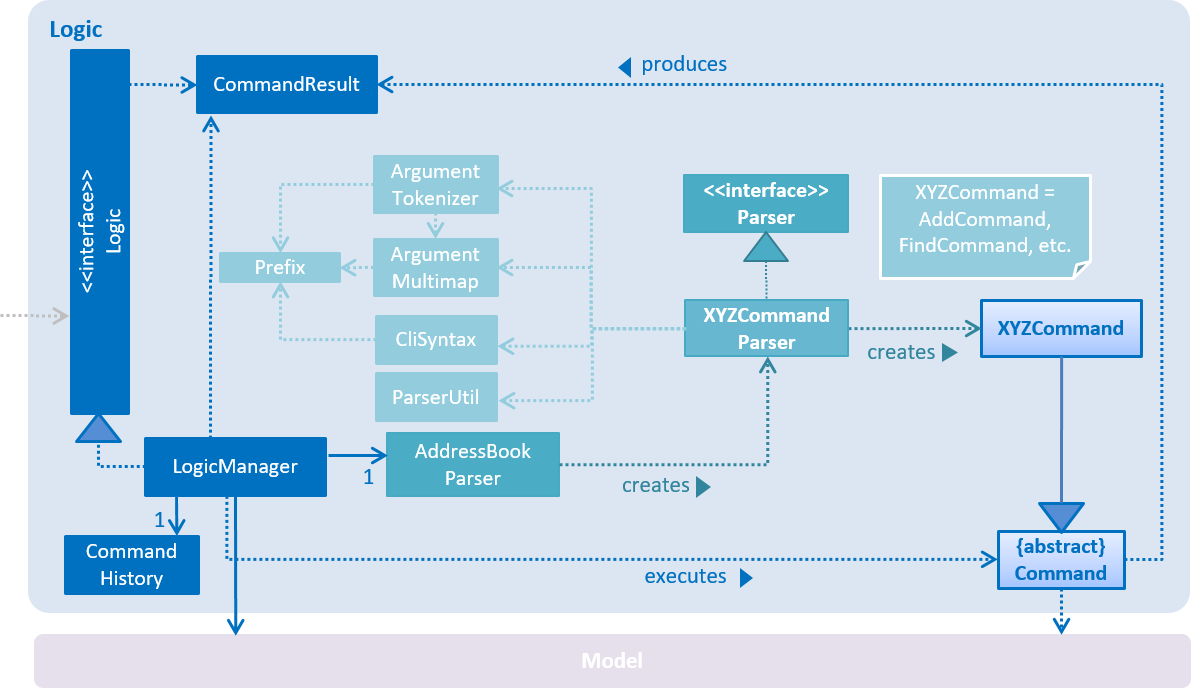
2.3. Logic component

API :
Logic.java
-
Logicuses theAddressBookParserclass to parse the user command. -
This results in a
Commandobject which is executed by theLogicManager. -
The command execution can affect the
Model(e.g. adding a person) and/or raise events. -
The result of the command execution is encapsulated as a
CommandResultobject which is passed back to theUi.
Given below is the Sequence Diagram for interactions within the Logic component for the execute("delete 1") API call.
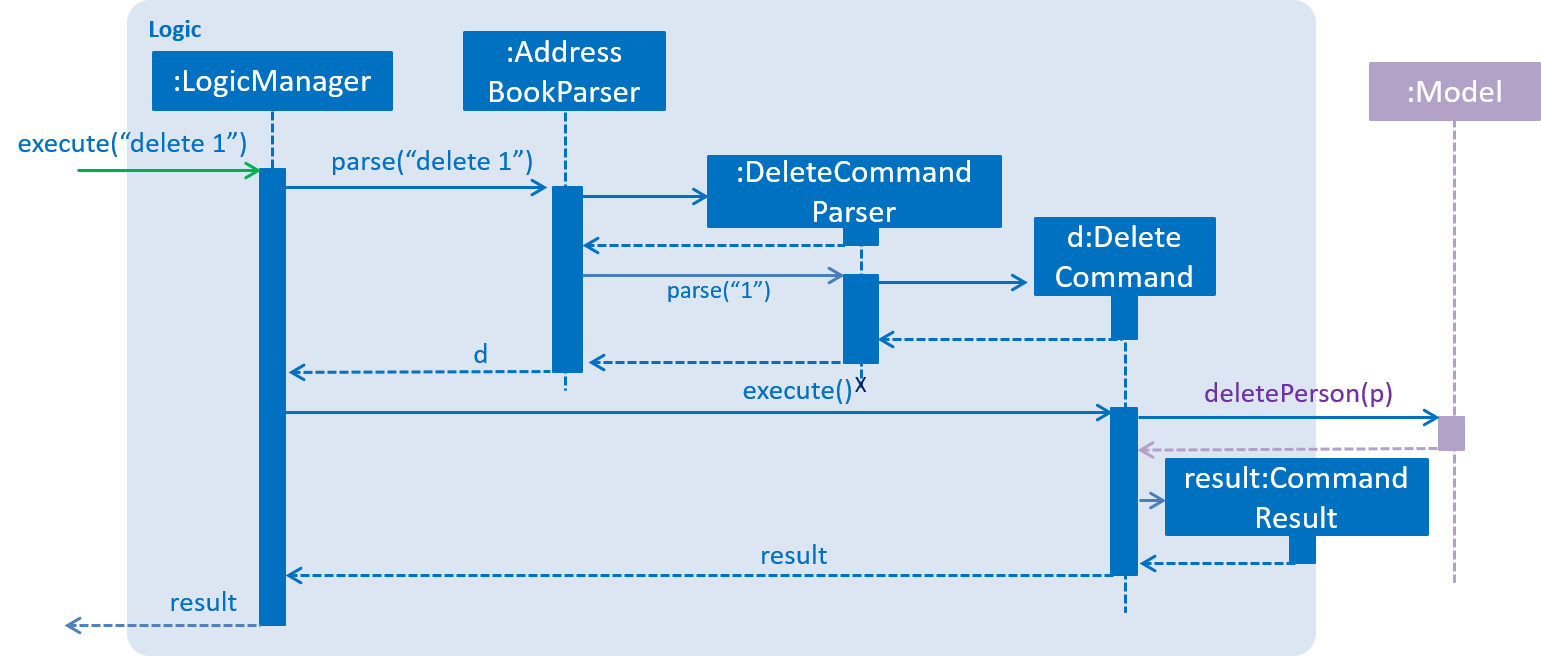
delete 1 Command2.4. Model component
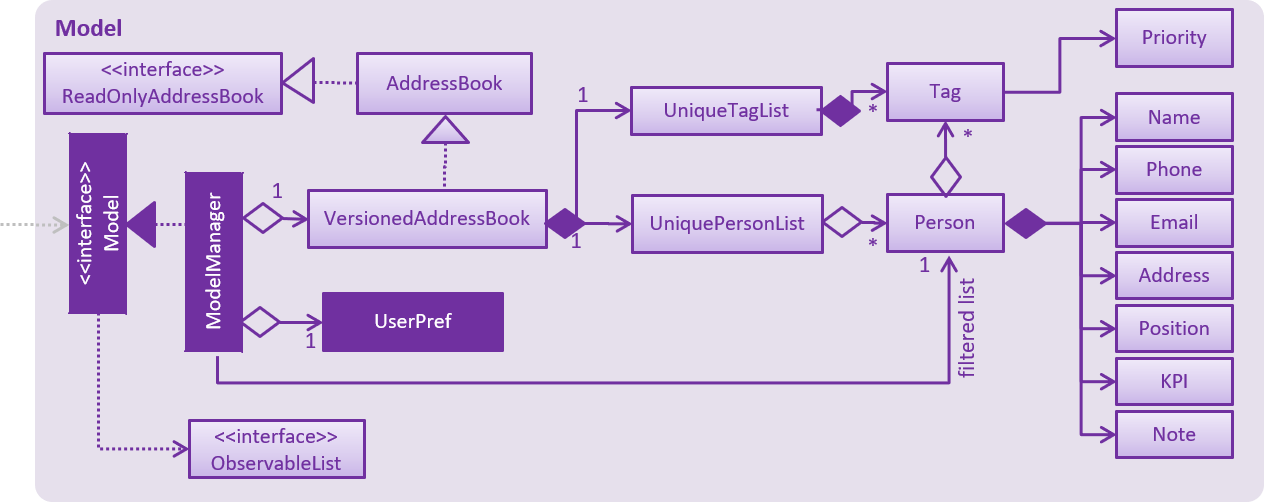
API : Model.java
The Model,
-
stores a
UserPrefobject that represents the user’s preferences. -
stores the Address Book data.
-
exposes an unmodifiable
ObservableList<Person>that can be 'observed' e.g. the UI can be bound to this list so that the UI automatically updates when the data in the list change. -
Stores a
UniqueTagListhashmap in theAddress Book. Each uniqueTagkey is assigned to a value of the list ofpersonwho are assigned with the same tag. -
does not depend on any of the other three components.
2.5. Storage component
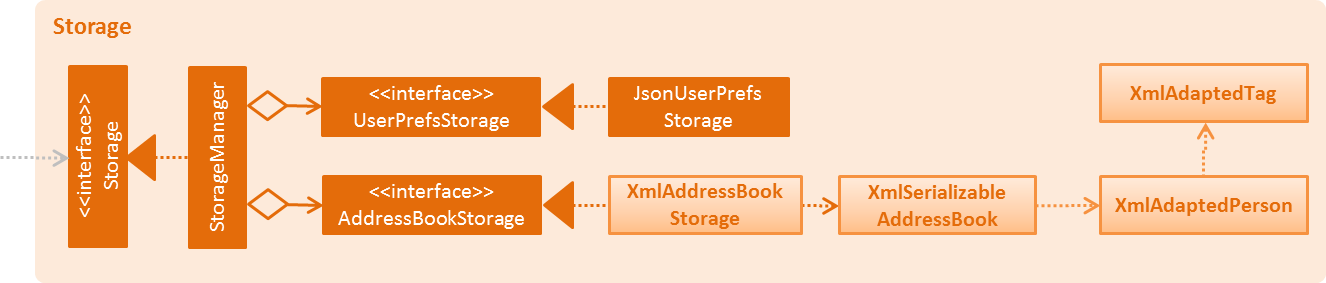
API : Storage.java
The Storage component,
-
can save
UserPrefobjects in json format and read it back. -
can save the Address Book data in xml format and read it back.
2.6. Common classes
Classes used by multiple components are in the seedu.addressbook.commons package.
3. Implementation
This section describes some noteworthy details on how certain features are implemented.
3.1. Undo/Redo feature
3.1.1. Current Implementation
The undo/redo mechanism is facilitated by VersionedAddressBook.
It extends AddressBook with an undo/redo history, stored internally as an addressBookStateList and currentStatePointer.
Additionally, it implements the following operations:
-
VersionedAddressBook#commit()— Saves the current address book state in its history. -
VersionedAddressBook#undo()— Restores the previous address book state from its history. -
VersionedAddressBook#redo()— Restores a previously undone address book state from its history.
These operations are exposed in the Model interface as Model#commitAddressBook(), Model#undoAddressBook() and Model#redoAddressBook() respectively.
Given below is an example usage scenario and how the undo/redo mechanism behaves at each step.
Step 1. The user launches the application for the first time. The VersionedAddressBook will be initialized with the initial address book state, and the currentStatePointer pointing to that single address book state.

Step 2. The user executes delete 5 command to delete the 5th person in the address book. The delete command calls Model#commitAddressBook(), causing the modified state of the address book after the delete 5 command executes to be saved in the addressBookStateList, and the currentStatePointer is shifted to the newly inserted address book state.
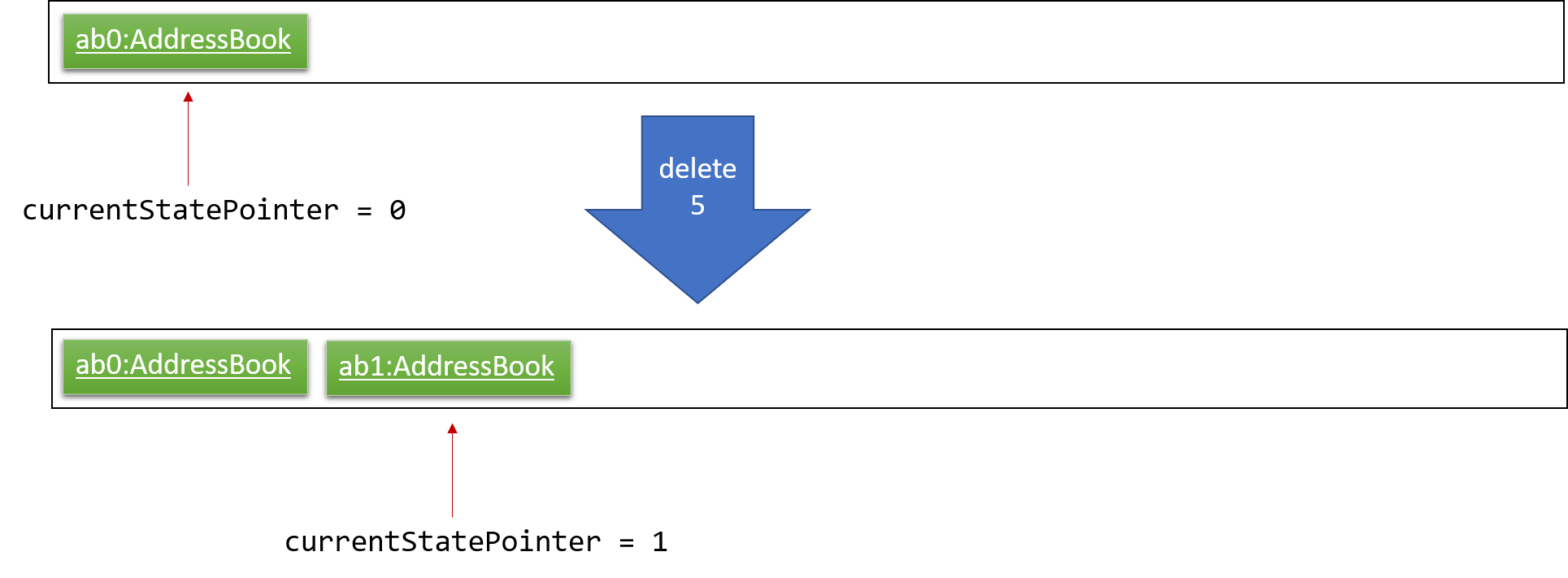
Step 3. The user executes add n/David … to add a new person. The add command also calls Model#commitAddressBook(), causing another modified address book state to be saved into the addressBookStateList.
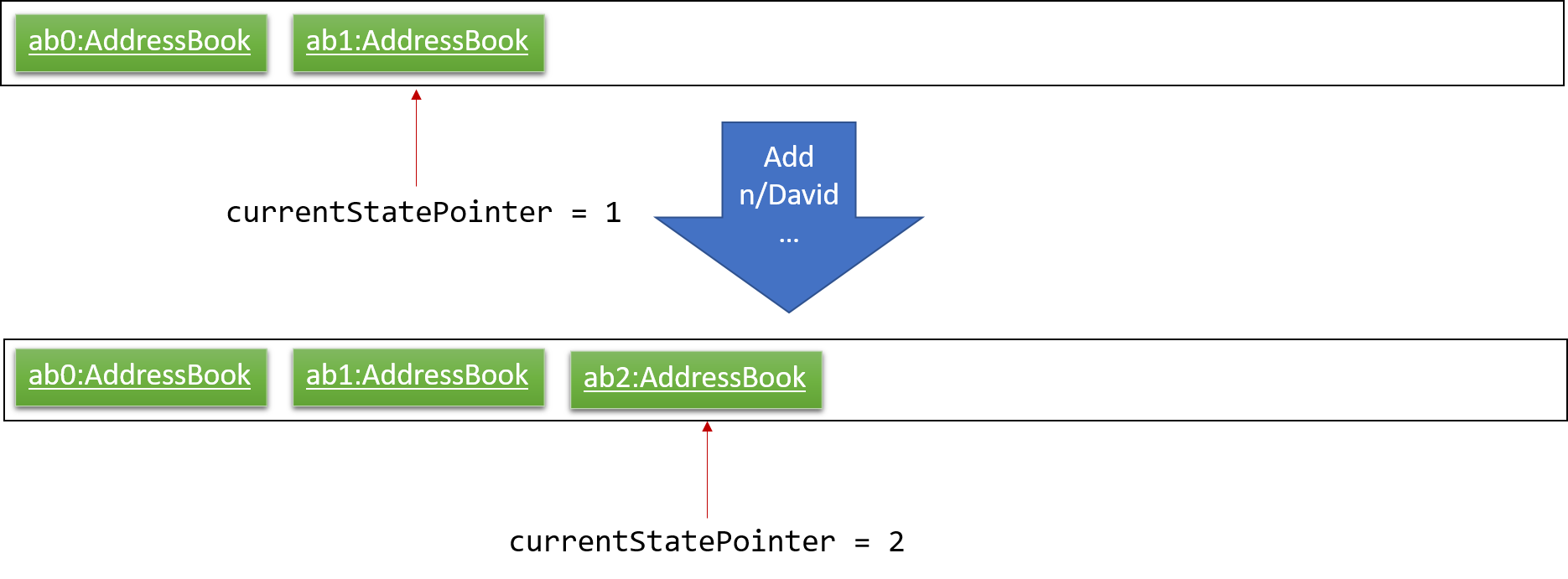
If a command fails its execution, it will not call Model#commitAddressBook(), so the address book state will not be saved into the addressBookStateList.
|
Step 4. The user now decides that adding the person was a mistake, and decides to undo that action by executing the undo command. The undo command will call Model#undoAddressBook(), which will shift the currentStatePointer once to the left, pointing it to the previous address book state, and restores the address book to that state.
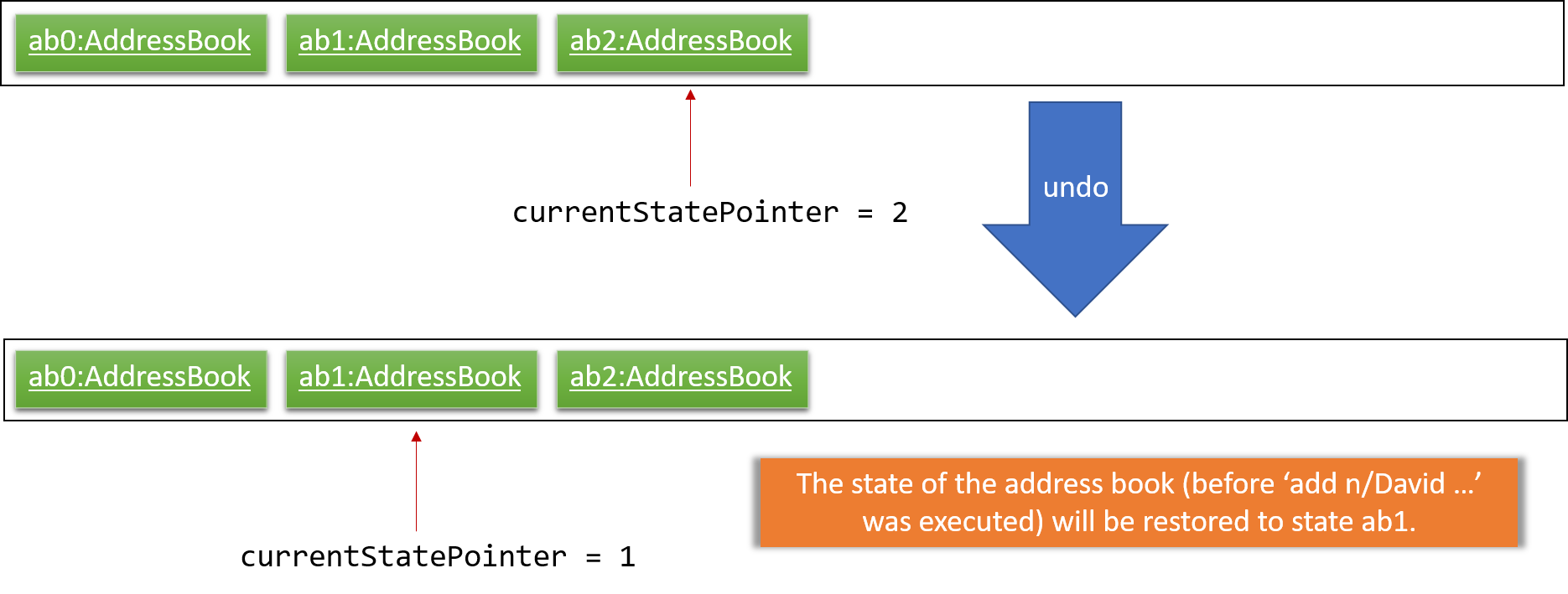
If the currentStatePointer is at index 0, pointing to the initial address book state, then there are no previous address book states to restore. The undo command uses Model#canUndoAddressBook() to check if this is the case. If so, it will return an error to the user rather than attempting to perform the undo.
|
The following sequence diagram shows how the undo operation works:
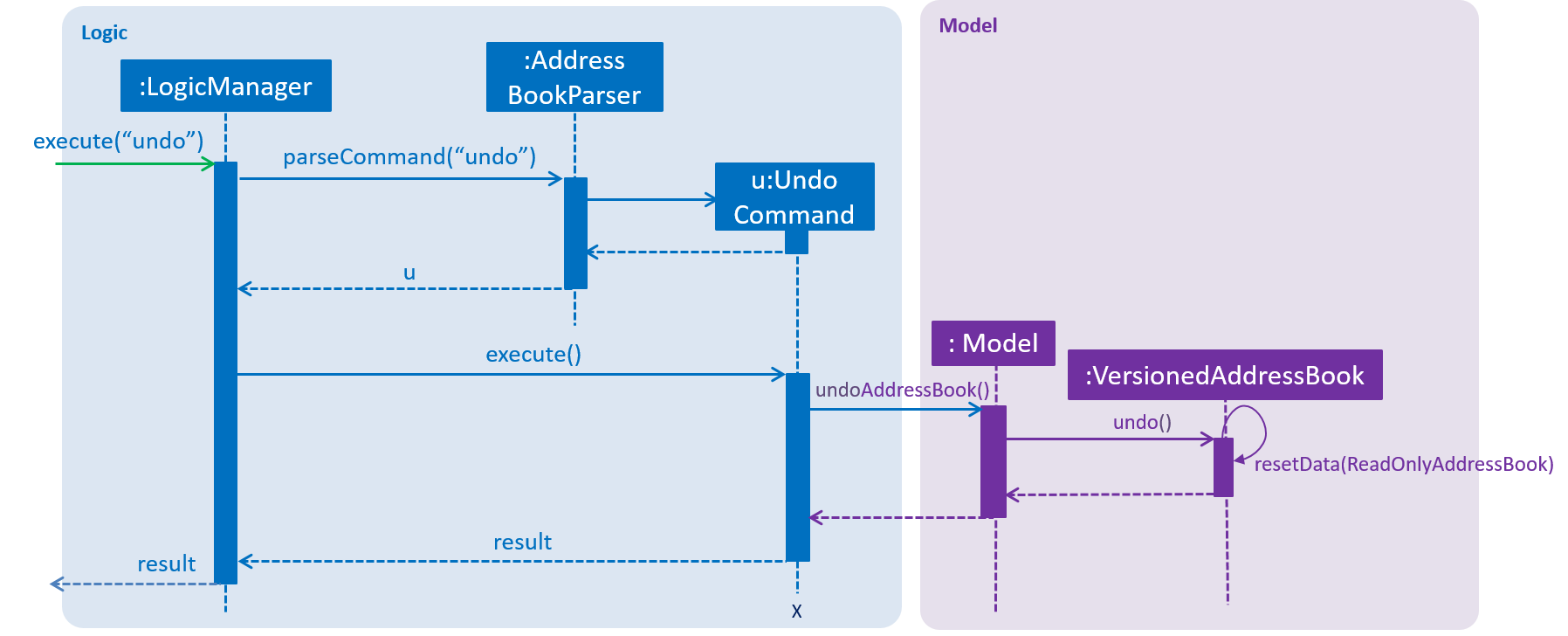
The redo command does the opposite — it calls Model#redoAddressBook(), which shifts the currentStatePointer once to the right, pointing to the previously undone state, and restores the address book to that state.
If the currentStatePointer is at index addressBookStateList.size() - 1, pointing to the latest address book state, then there are no undone address book states to restore. The redo command uses Model#canRedoAddressBook() to check if this is the case. If so, it will return an error to the user rather than attempting to perform the redo.
|
Step 5. The user then decides to execute the command list. Commands that do not modify the address book, such as list, will usually not call Model#commitAddressBook(), Model#undoAddressBook() or Model#redoAddressBook(). Thus, the addressBookStateList remains unchanged.
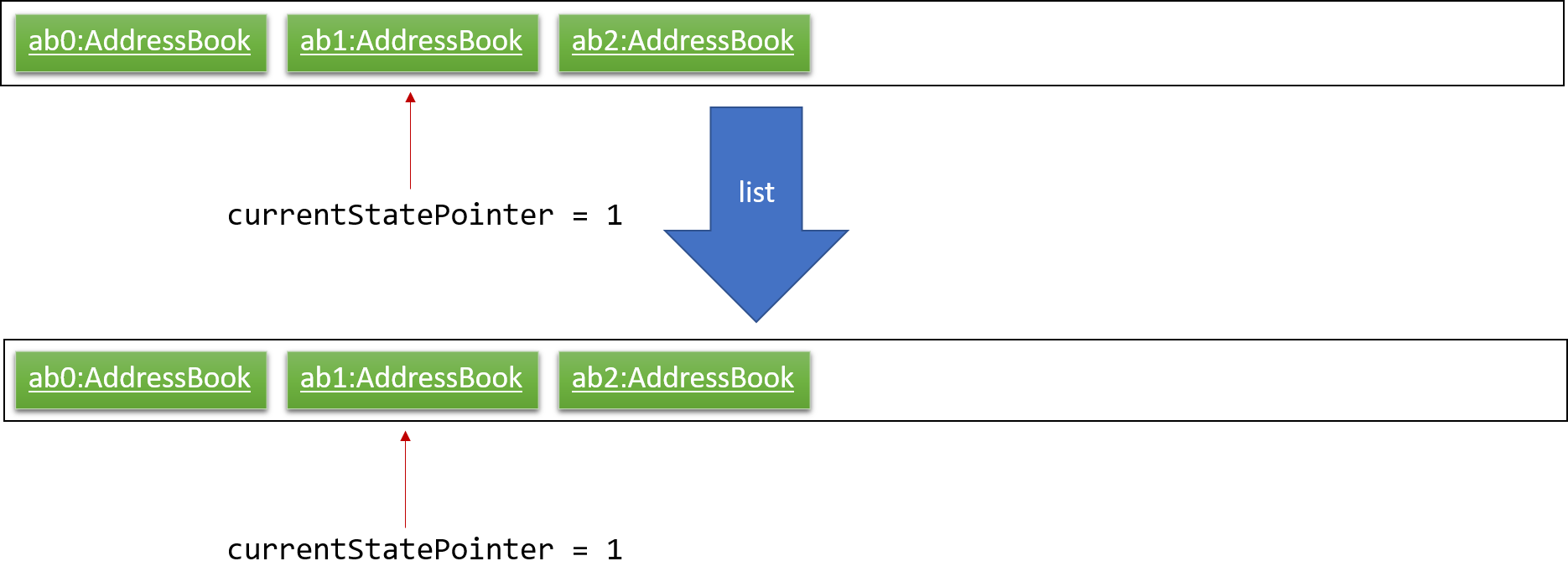
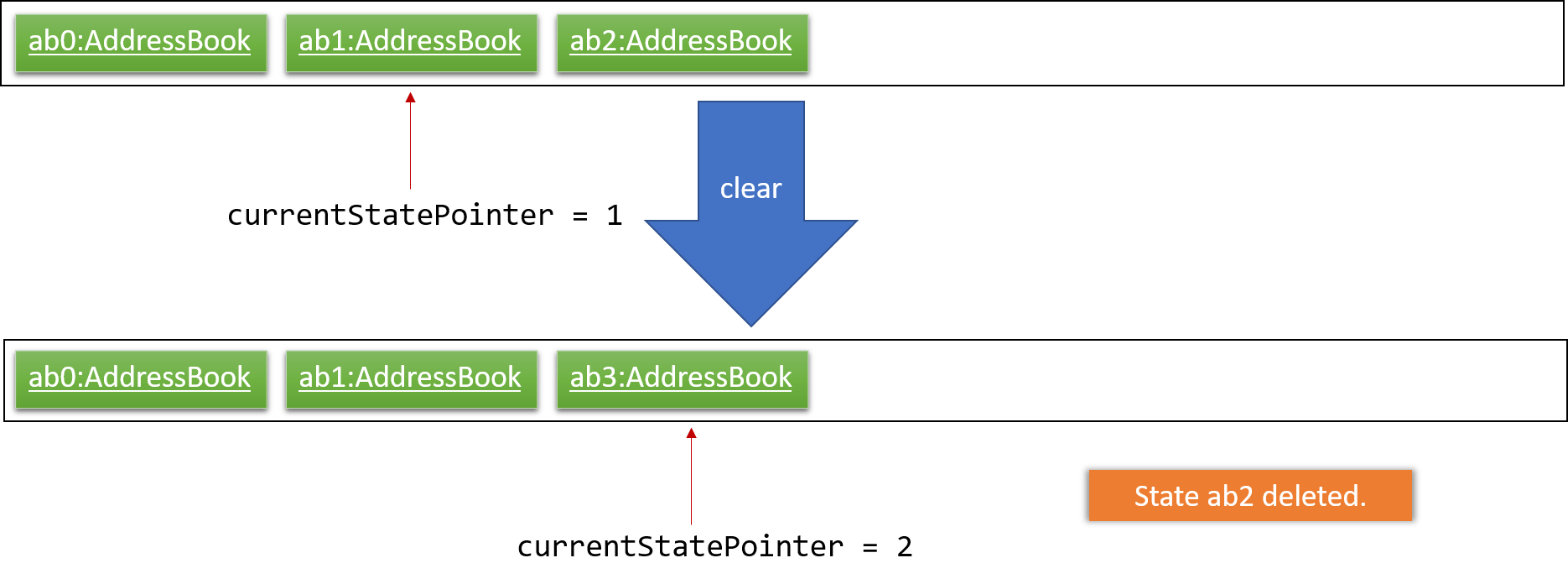
Step 6. The user executes clear, which calls Model#commitAddressBook(). Since the currentStatePointer is not pointing at the end of the addressBookStateList, all address book states after the currentStatePointer will be purged. We designed it this way because it no longer makes sense to redo the add n/David … command. This is the behavior that most modern desktop applications follow.
The following activity diagram summarizes what happens when a user executes a new command:

3.1.2. Design Considerations
Aspect: How undo & redo executes
-
Alternative 1 (current choice): Saves the entire address book.
-
Pros: Easy to implement.
-
Cons: May have performance issues in terms of memory usage.
-
-
Alternative 2: Individual command knows how to undo/redo by itself.
-
Pros: Will use less memory (e.g. for
delete, just save the person being deleted). -
Cons: We must ensure that the implementation of each individual command are correct.
-
Aspect: Data structure to support the undo/redo commands
-
Alternative 1 (current choice): Use a list to store the history of address book states.
-
Pros: Easy for new Computer Science student undergraduates to understand, who are likely to be the new incoming developers of our project.
-
Cons: Logic is duplicated twice. For example, when a new command is executed, we must remember to update both
HistoryManagerandVersionedAddressBook.
-
-
Alternative 2: Use
HistoryManagerfor undo/redo-
Pros: We do not need to maintain a separate list, and just reuse what is already in the codebase.
-
Cons: Requires dealing with commands that have already been undone: We must remember to skip these commands. Violates Single Responsibility Principle and Separation of Concerns as
HistoryManagernow needs to do two different things.
-
3.2. Data Encryption
3.2.1. Current Implementation
The encrypt/ decrypt mechanism is facilitated by FileEncryptor.
It extends AddressBook with a encrypt/decrypt feature, maintained by PasswordCommand.
Additionally, it implements the following operations:
-
FileEncryptor#process()— Decrypts or encrypts the data file depending on its current state (encrypted or decrypted). -
VersionedAddressBook#decryptFile()— encrypts a file given the path and password. -
VersionedAddressBook#encryptFile()— decrypts a file given the path and password.
Given below is an example usage scenario and how the password mechanism behaves at each step.
Step 1. The user enters the password command with a password.
If the user enters a password which is non alpha-numeric, an error will be thrown at the CommandResult box. Only alpha-numeric passwords are supported by FileEncryptor
|
Step 2. The user closes the address book.
Step 3. The user re-opens the address book. No data will be shown as the XML data file is technically not present in the data folder.
Step 4. The user enters the password command with the right password. Address book will be refreshed and restored back to its former state (before encryption).
| If the user enters the wrong password , an error will be thrown at the CommandResult box. |
3.2.2. Design Considerations
Aspect: How encryption and decryption is done
-
The
PBEKeySpecis first specified using the "PBEWithMD5AndDES" specification. -
A secret key is generated from
SecretKeyFactoryusing "PBEWithMD5AndDES" cipher. -
A
Cipheris then used to encrypt or decrypt the file with a given password and key specifications. -
Additional salt is used in the password to ensure that the password cannot be easily broken down by dictionary attacks.
Aspect: Pros and cons of tight security
-
Pros: Your data is protected and it will be near impossible to use any third part tool to crack the data file.
-
Cons: Data will be permanently lost if you forget the password.
Encrypting the address book:
Step 1. The user executes password test to encrypt the address book with test as the password.
Step 2. PasswordCommandParser checks for the validity of the input password (if its alpha-numeric)
Step 3. If the password is acceptable, it is parsed to the PasswordCommand object
Step 4. Within the PasswordCommand object, a new FileEncryptor object is created and it will check if the address book is currently in a locked state
Step 5. If it is not currently locked, it will create a cipher and begin encrypting the address book with the input password.
Step 6. Previous addressbook.xml will be deleted whereas a new addressbook.xml.encrypted file will be created.
Step 7. A new emptyPredicate object will be instantiated and model.updateFilteredPersonList(emptyPredicate) will be called to clear the address book list.
Step 8. A CommandResult object will be created to notify the user that the encryption was successful
Accessing commands post encryption:
Step 1. The user executes list to list out all the contacts in the address book.
Step 2. The user input is parsed by AddressBookParser which creates a new ListCommandParser object.
Step 3. The arguments are then parsed by the ListCommandParser.
Step 4. ListCommandParser then checks the validity of the arguments before it creates the ListCommand object.
Step 5. ListCommand creates a FileEncryptor object to check if the address book is in a locked state by calling the islocked() method.
Step 6. isLocked() will return true.
Step 7. A CommandException will be thrown to warn the user that the address book is in a locked state.
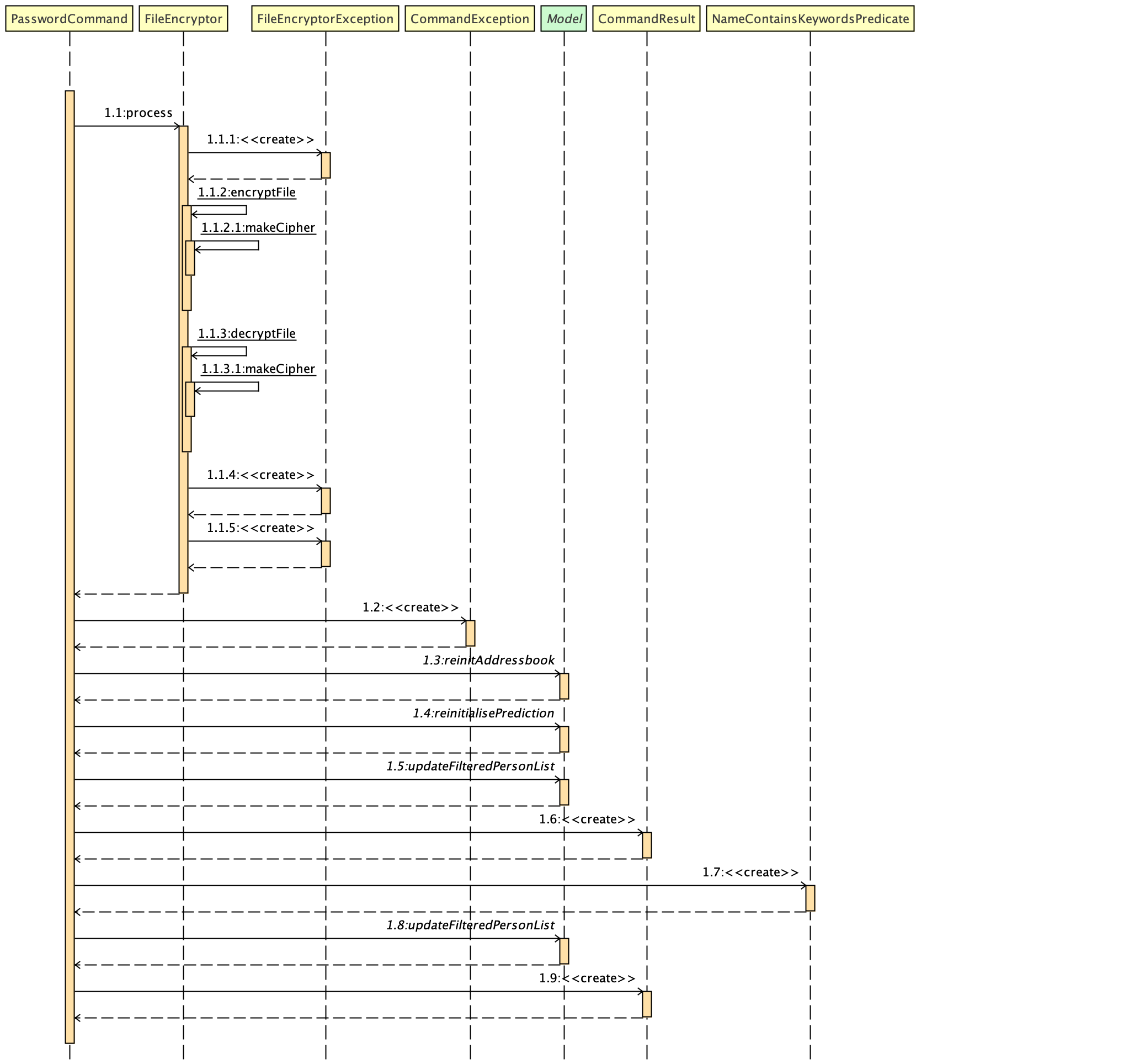
Figure 1. Interactions inside the logic component for the password command.
3.3. Logging
We are using java.util.logging package for logging. The LogsCenter class is used to manage the logging levels and logging destinations.
-
The logging level can be controlled using the
logLevelsetting in the configuration file (See Section 3.4, “Configuration”) -
The
Loggerfor a class can be obtained usingLogsCenter.getLogger(Class)which will log messages according to the specified logging level -
Currently log messages are output through:
Consoleand to a.logfile.
Logging Levels
-
SEVERE: Critical problem detected which may possibly cause the termination of the application -
WARNING: Can continue, but with caution -
INFO: Information showing the noteworthy actions by the App -
FINE: Details that is not usually noteworthy but may be useful in debugging e.g. print the actual list instead of just its size
3.4. Configuration
Certain properties of the application can be controlled (e.g App name, logging level) through the configuration file (default: config.json).
3.5. Text Prediction
3.5.1. Current Implementation
The text prediction feature is facilitated mainly by 2 classes, CommandCompleter and Trie. Trie contains the underlying data structure with a set of operations that allows predictions to be retrieved. CommandCompleter manages several instances of that data structure such that predictions of different attributes (name, email, address, etc.) and command keywords (add, edit, etc.) can be made.
For Trie, following operations are implemented:
-
Trie#insert(String value)— inserts a string into the data structure. -
Trie#remove(String value)— removes a string from the data structure. -
Trie#getPredictList(String prefix)— retrieves a list of predicted string values that completes the prefix.
For CommandCompleter, following operations are implemented:
-
CommandCompleter#insertPerson()— inserts a Person’s attributes into respective data structure instances. -
CommandCompleter#removePerson()— removes a Person’s attributes from respective data structure instances. -
CommandCompleter#editPerson()— edits a Person’s attributes in each data structure instances. -
CommandCompleter#predictText()— predicts a list of possible text outputs that will complete and append to the given text input. -
CommandCompleter#clearData()— clears all data structure instances of their data.
Given below is an example usage scenario and how the text prediction mechanism behaves on a high level. For low level implementation details, refer to Appendix A, Text Prediction low level details.
Step 1. User launches the application. CommandCompleter is instantiated and will initialise all Trie instances with all command keywords and every existing contact’s (aka Person) attributes (name, phone, address, etc.).
Step 2. The user keys in find n/Al into the command box and presses Tab. This will invoke predictText(). The method will subsequently determine (assisted by several helper classes) which Trie instance to retrieve the predictions from. That Trie instance then returns a list of possible predictions, in this case, a list containing ex Yeoh.
Step 3. The user decides to add a new contact with the name Alex Tan using the add command. In the add logic, the method Model#insertPersonIntoPrediction(Person person) will be called which will call the insertPerson() method. This method inserts the contact’s (Alex Tan) attributes into the respective Trie instances.
Step 4. The user decides to predict find n/Al again. The logic sequence is similar to Step 2. However, since a new contact was added in Step 3, instead of returning ex Yeoh only, the returning list will contain both ex Yeoh and ex Tan.
Step 5. The user now decides to remove the contact with the name Alex Yeoh from the address book using the delete 1 command. The removePerson() method will be called and removes that contact’s (Alex Yeoh) attributes from the respective Trie instances.
Step 6. The user decides to predict find n/Al again. Similar to Step 4 except that Alex Yeoh has been removed, the list returned will contain only ex Tan.
Step 7. The user decides to clear the address book with clear command which invokes clearData() method. This clears all attributes data in all Trie instances.
Step 8. The user wants to predict find n/Al again. However since all data were cleared, the returned predictions list contains no entries. No predictions are displayed in feedback panel.
The sequence diagram below demonstrates how the predictText() method will work:
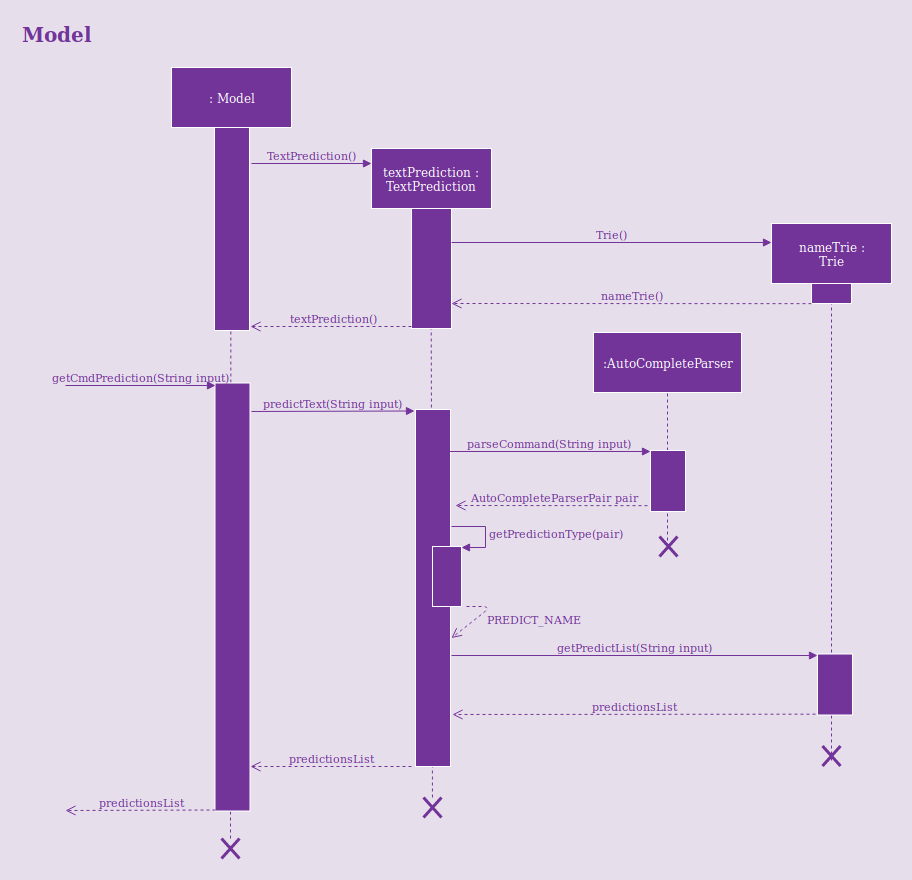
3.5.2. Design Considerations
Aspect: Data structure used to support text prediction
-
Alternative 1 (current choice): Use a Directed Acyclic Graph to store strings.
-
Pros: Results in greater computational efficiency than the naive approach (Alternative 2).
-
Cons: Much more difficult to implement and prone to bugs.
-
-
Alternative 2: Use a simple list to store strings.
-
Pros: Much more easier and simple to implement.
-
Cons: Inefficient and takes longer time to retrive the strings. Since the address book can potentially contain large number of contacts, retrieval of strings may take too long, which results in a slow application.
-
3.6. Email Contacts
3.6.1. Current Implementation
The email feature is facilitated by the MailCommand class. It is assisted by the MailCommandParser class to determine the mailType (who to email to) based on the user input. It is also supported by the Java built-in Desktop class to open the user system’s email application using the mail type as the recipients. It implements the following operation:
-
MailCommand#execute()- opens user system’s email application based on themailType.
Given below is an example usage scenario and how the email mechanism behaves at each step:
Step 1. The user selects contact with the index 1 using the select command.
Step 2. The user inputs mail into the command box and executes the command. execute() checks if the user system is supported by the Java Desktop library and throws an exception if unsupported. In this case, the mailType is contacts selection type. Hence, MailCommand#mailToSelection() is invoked. The Uniform Resource Identifier (URI) is built and Desktop#mail(URI uri) is called, which opens up the system’s email application.
If the user decides to email all contacts with the tag coworker instead, the user will execute mail t/coworker in the command box. Similar to Step 2, except that the logic calls MailCommand#mailToGroups(Model model, Tag tag) with the input tag as parameter. URI is built with contacts containing the specified tag and the email application opens up.
|
3.7. Back Up and Restore
3.7.1. Current implementation of backup
Creation of backups is done in BackUpCommand class. It extends the Command class with an overriding execute function.
Model
This feature implements a new method in Model
-
Model#backUpAddressbook(Path)— Saves a copy of the address book into the path in aXMLformat.
3.7.2. Current implementation of Listing of backup snapshots
Listing of the snapshots of backups is done with the RestoreSnapshotsCommand class. It also extends the Command class.
BackupList
The BackupList object holds a map of files with indexes as its keys. It also has an array of String. The position of the strings corresponds to the index of the file it represents in the map.
-
BackupList#getFileName()— returns a list of the names of the snapshots. -
BackupList#getFileMap()— returns a map of the snapshots, each denoted with anINDEX -
BackupList#millisToDateAndTime(String fileName)— converts a timestamp in milliseconds to a formatted date and time format.
3.7.3. Current implementation of Restoring from the list
The restoration of backup snapshots is done in the RestoreCommand class. It extends the Command class with an overriding execute function.
Model
This feature implements a new method in Model
-
Model#replaceData(Path path)— Overrides the current address book information with anotherXMLfile.
3.7.4. Usage Scenarios
Given below is the sequence of actions done by the address book when you back up and restore your data.
Saving a Backup
Step 1. The user executes backup to create a backup snapshot
Step 2. The user input is first parsed by AddressBookParser which creates a new BackupCommand object.
Step 3. BackupCommand is executed and calls Model#backUpAddressbook(Path) with the path of the .backup folder as the argument. This creates a copy of the address book data in the folder as an XML file.
Step 4. An AddressBookStorage will be created in the Model#backUpAddressbook(Path) method which facilitates the saving of the data of address book.
Step 5. saveAddressBook() will be called to save the data of the address book.
AddressBookStorage will check if the .backup folder exists. If not it will create the folder. |
The following sequence diagrams shows you how the add operation works:
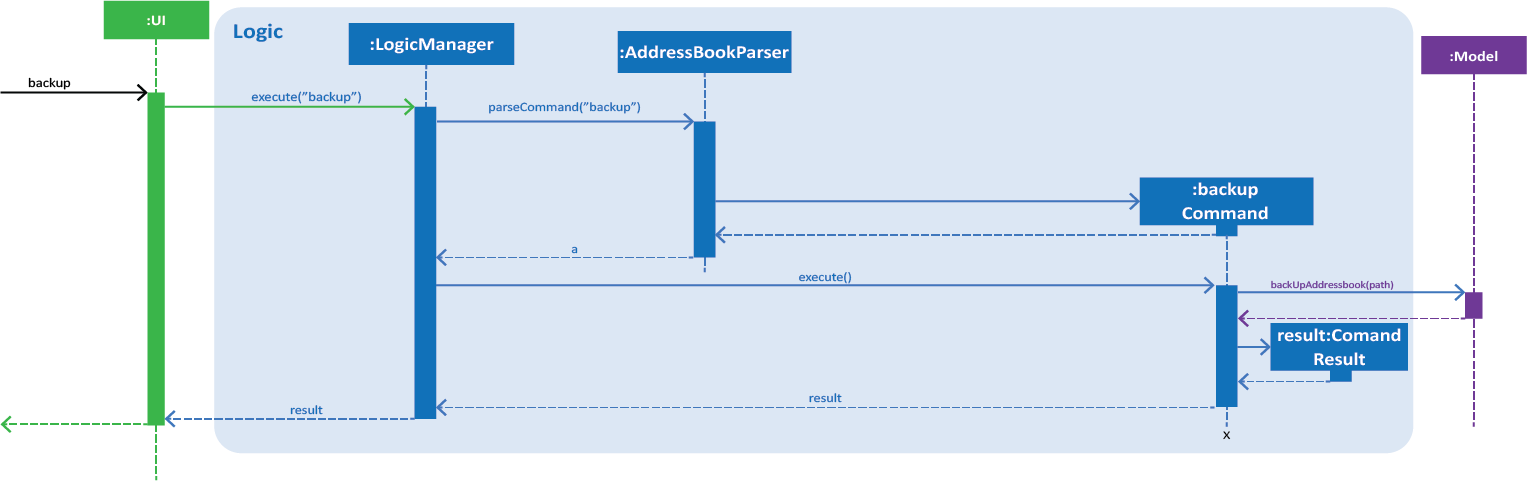
Figure 1. Interactions inside the Logic component for the backup command.
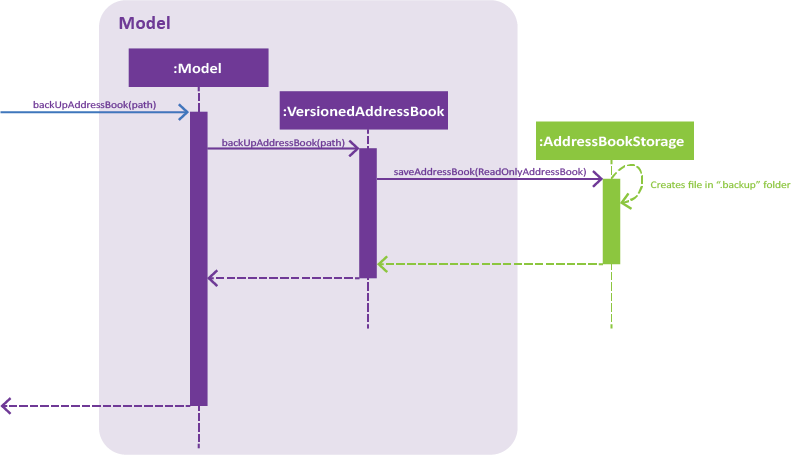
Figure 2. Interactions inside the Storage component for the backup command.
Listing all the snapshots
Step 1. The user executes restore-snapshots to get a list of all backup snapshots
Step 2. The user input is first parsed by AddressBookParser which creates a new RestoreSnapshotsCommand object.
Step 3. RestoreSnapshotsCommand is executed and calls readBackupList(String) with the directory of the .backup folder as the argument. This reads a BackupList from the given destination path. A list of formatted file names will be created which will be shown to the user.
The following sequence diagrams shows you how the add operation works:
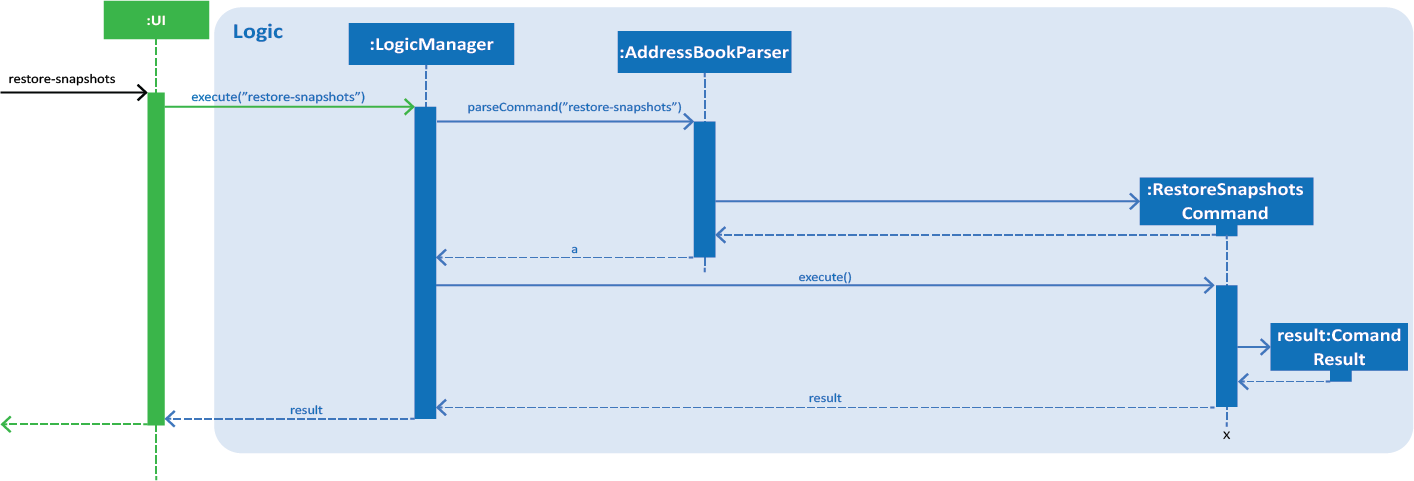
Figure 3. Interactions inside the Logic component for the restore-snapshots command.
Restoring from a backup
Step 1. The user executes restore 1 to restore their data with a backup snapshot denoted by an index of 1
Step 2. The user input is first parsed by AddressBookParser which creates a new RestoreCommandParser object.
Step 3. The argument, 1, is then parsed by RestoreCommandParser.
Step 4. RestoreCommandParser checks the validity of the index as input by the user. It then creates a
BackupList object.
If the index is not valid, an error would be returned to the user instead of creating a RestoreCommand object.
|
Step 5. RestoreCommandParser then creates a new RestoreCommand with the BackupList and index as its arguments.
Step 6. RestoreCommand is executed and calls Model#replaceData(Path) which replaces the data of the address book with the XML file denoted by the Path.
Before calling Model#replaceData(Path path), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
Step 7. A XmlAddressBookStorage will be initialised which helps to read the data of the XML file.
Step 8. The address book will be overwritten with the new data by calling resetData with the new data as its argument.
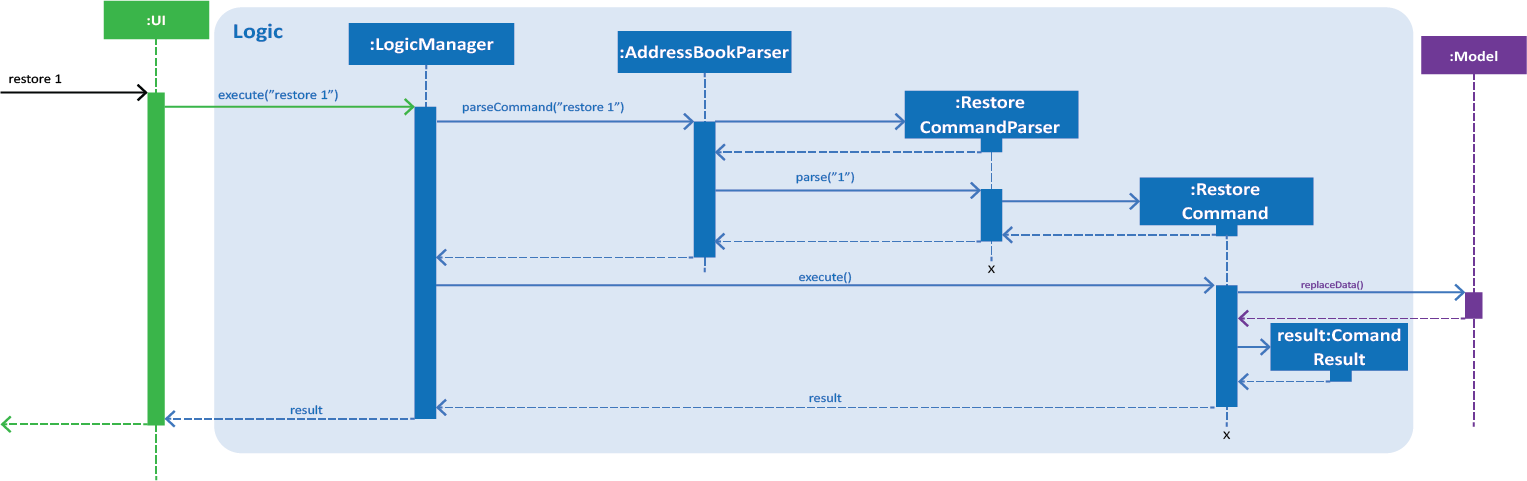
Figure 4. Interactions inside the Logic component for the restore 1 command.
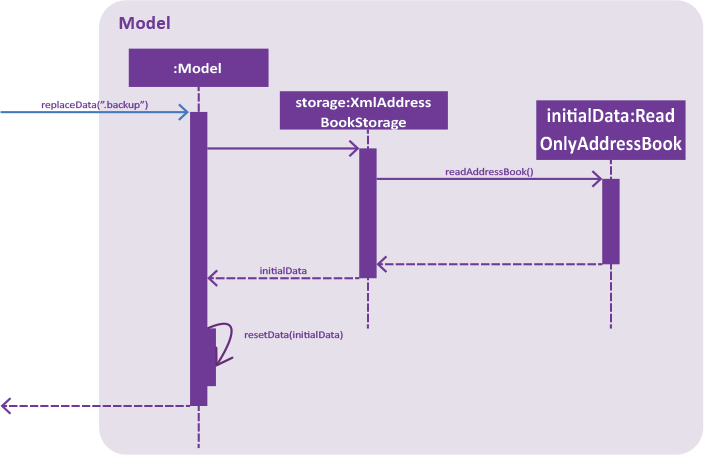
Figure 5. Interactions inside the Storage component for the restore 1 command.
3.8. Export and Import
3.8.1. Current implementation of Export
The export function is facilitated by the ExportCommand class. It extends the Command class wit an overriding execute function.
CsvWriter
CsvWriter is an object that takes in a path of where the export is to be saved and write a CSV file into the said path.
The conversion is as follows:
Step 1. The constructor converts an ObservableList<Person> into a List<Person>
Step 2. The convertToCsv() method will be called in ExportCommand and a new CSV file will be written with the content of the created List<Person>.
Step 3. This file will be created in the path.
3.8.2. Current implementation of Import
The import function is implemented with the ImportCommand class. It extends the Command class with an overriding execute method.
CsvReader
CsvReader is an object that takes in a CSV file and converts it into a list of persons.
The conversion is as follows:
Step 1. The constructor reads a CSV file line by line.
Step 2. The convertToList method formats the file into a Model friendly format.
Step 3. It then converts the strings into a persons.
Step 4. These persons are then stored in a List<Person> and returned.
3.8.3. Usage Scenarios
Given below is the sequence of actions done by the address book when you export and import an address book.
Exporting your address book
Step 1. The user executes export d/C:\Users\USER\Desktop\DemoExport f/test to export their data to the directory with the file name the user wants.
Step 2. The user input is first parsed by AddressBookParser which creates a new ExportCommandParser object.
Step 3. The argument, d/C:\Users\USER\Desktop\DemoExport f/test, is then parsed by ExportCommandParser.
Step 4. ExportCommandParser checks the validity of the directory as input by the user. It then creates a
ExportCommand object with the directory and file name as its arguments.
If the directory is not valid or a file with the same file name exists in the directory, an error would be returned to the user instead of creating a ExportCommand object. |
Step 5. ExportCommand is executed and creates a CsvWriter object. The CsvWriter object is created with a copy of the address book taken from Model
Step 6. convertToCsv(String directory) is called with the full directory as the argument which writes the data of the address book to a file of CSV format.
Before calling convertToCsv(String directory), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
The following sequence diagrams shows you how the add operation works:
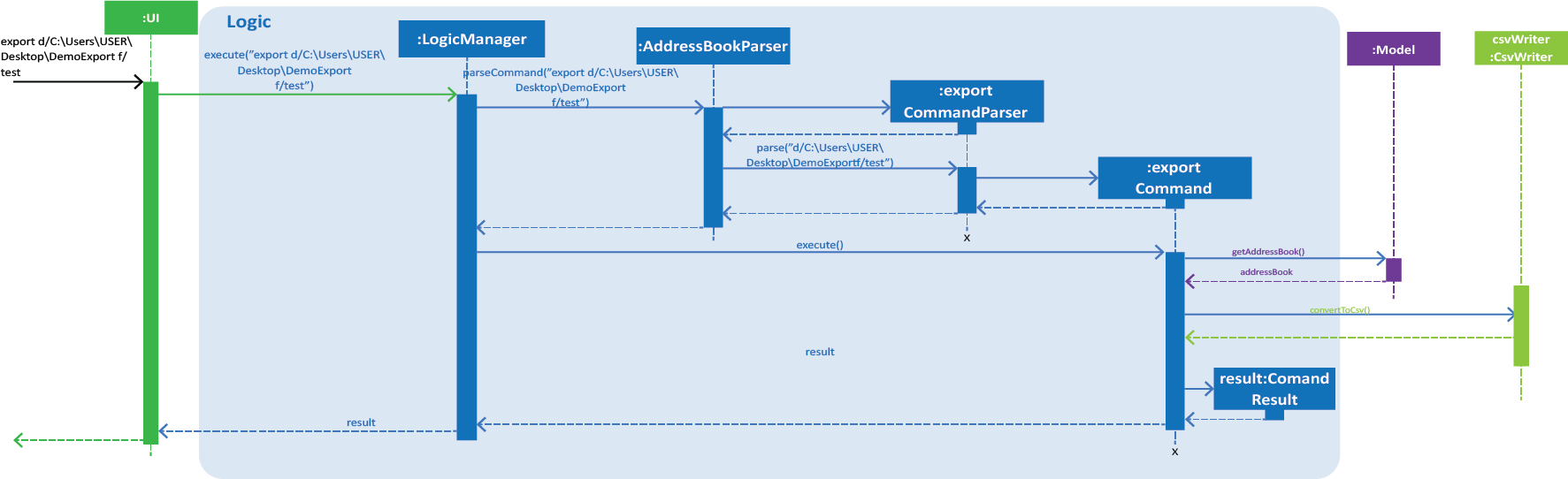
Figure 1. Interactions inside the Logic component for the export d/C:\Users\USER\Desktop\DemoExport f/test command.
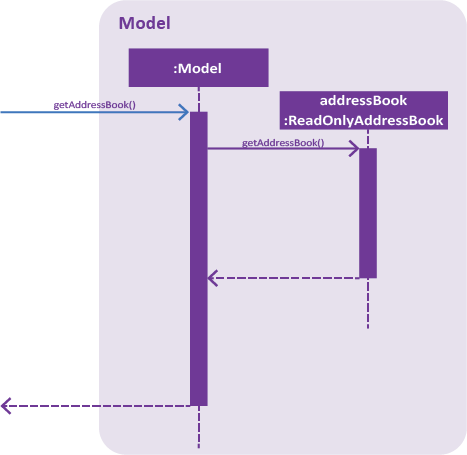
Figure 2. Interactions inside the Storage component for the export d/C:\Users\USER\Desktop\DemoExport f/test command.
Importing to your address book
Step 1. The user executes import d/C:\Users\USER\Desktop\DemoExport f/test to import their data from the directory with the name of the file.
Step 2. The user input is first parsed by AddressBookParser which creates a new ImportCommandParser object.
Step 3. The argument, d/C:\Users\USER\Desktop\DemoExport f/test, is then parsed by ImportCommandParser.
Step 4. ImportCommandParser checks the validity of the directory as input by the user. It then creates a
ImportCommand object with the directory and file.
If the directory is not valid or a file with the name does not exists in the directory, an error would be returned to the user instead of creating a ImportCommand object.
|
If the file is of the wrong format, an error would also be returned to the user instead of creating a ImportCommand object.
|
Step 5. ImportCommand is executed and creates a CsvReader object. The CsvReader object is created with the file identified
Step 6. convertToList() is called which creates a list of persons that can be added.
Before calling convertToList(), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
Step 7. There is a loop that iterates through the list and add the persons into the address book. All duplicated persons will be skipped.
The following sequence diagrams shows you how the add operation works:
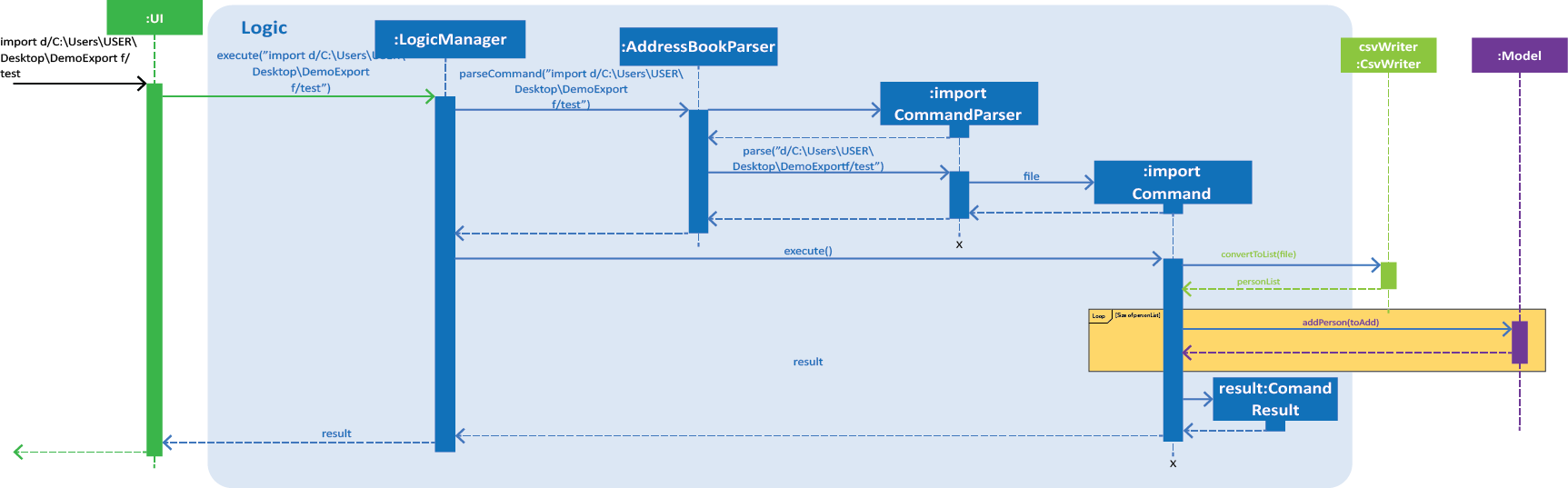
Figure 1. Interactions inside the Logic component for the import d/C:\Users\USER\Desktop\DemoExport f/test command.
3.9. Find and Search
3.9.1. Current Implementation
The find function has been revamped to support search guessing and search by attributes.
FindCommand is now backed up by the ClosestMatchList class which uses LevenshteinDistanceUtil and HammingDistanceUtil to generate an ordered set of Person attributes ordered by similarity.
3.9.2. Design Considerations
Aspect: How find command executes
-
Alternative 1: Find using only predicates
-
Pros: Easy to implement.
-
Cons: Search must be exact, cannot have typos or incomplete keywords
-
-
Alternative 2: Store the search results in a
treeMapordered by their Levenshtein or Hamming distances from the search keyword-
Pros: Will also consider searches that are similar to what we want and will account for typos or incomplete keywords
-
Cons: Added complexities in finding and searching, can be vague when searching for number attributes
-
-
Alternative 3 (current choice): Same as alternative 2 but we use Hamming distance for phone numbers and KPI attributes instead.
-
Pros: Phone number and KPI searches are now more precise
-
Cons: Added complexities in finding and searching
-
Aspect: Expanded features of find command
-
Alternative 1: Find only by name
-
Pros: Easy to implement.
-
Cons: Can only search by name of addressees
-
-
Alternative 2: Find by attributes
-
Pros: Can search by email, phone, address, etc instead of just the name of addressees
-
Cons: Can only search for one attribute at a time (i.e find by name or find by email)
-
-
Alternative 3 (current choice): Chain-able find attributes
-
Pros: Can search by email and phone and address, etc instead of just one at a time
-
Cons: Added complexities in find command
-
Aspect: Data structure to support the revamped Find command
treeMap was used to store the search results ordered by their Levenshtein or Hamming distances.
The results are then filtered and
results furthest away from the top few are ignored. The searches will then be passed thru their respective predicates
(NameContainsKeywordsPredicate, AddressContainsKeywordsPredicate, EmailContainsKeywordsPredicate, KpiContainsKeywordPredicate, NoteContainsKeywordsPredicate, PhoneContainsKeywordPredicate, PositionContainsKeywordsPredicate, TagContainsKeywordsPredicate)
before filtering the list.
Searching for a contact:
Step 1. The user executes find a/Clementi t/owesMoney to find all contacts staying in Clementi and bearing the owesMoney tag.
Step 2. The user input is parsed by AddressBookParser which creates a new FindCommandParser object.
Step 3. The arguments a/Clementi t/owesMoney are then parsed by the FindCommandParser.
Step 4. FindCommandParser then checks the validity of the arguments before it creates the FindCommand object.
Step 5. FindCommand then proceeds to create ClosestMatchList objects.
Step 6. It uses the list of keywords obtained from ClosestMatchList to create AddressContainsKeywordsPredicate and TagContainsKeywordsPredicate.
Step 7. These predicates are combined into a combinedPredicate object using the "AND" operation.
Step 8. The model is then updated by calling model.updateFilteredPersonList(combinedPredicate) together with the combined predicate obtained in Step 8.
Step 9. A CommandResult object will be created and an internal method findActualMatches() will be called to generate a string of keywords that are exact matches and keywords that are guessed.
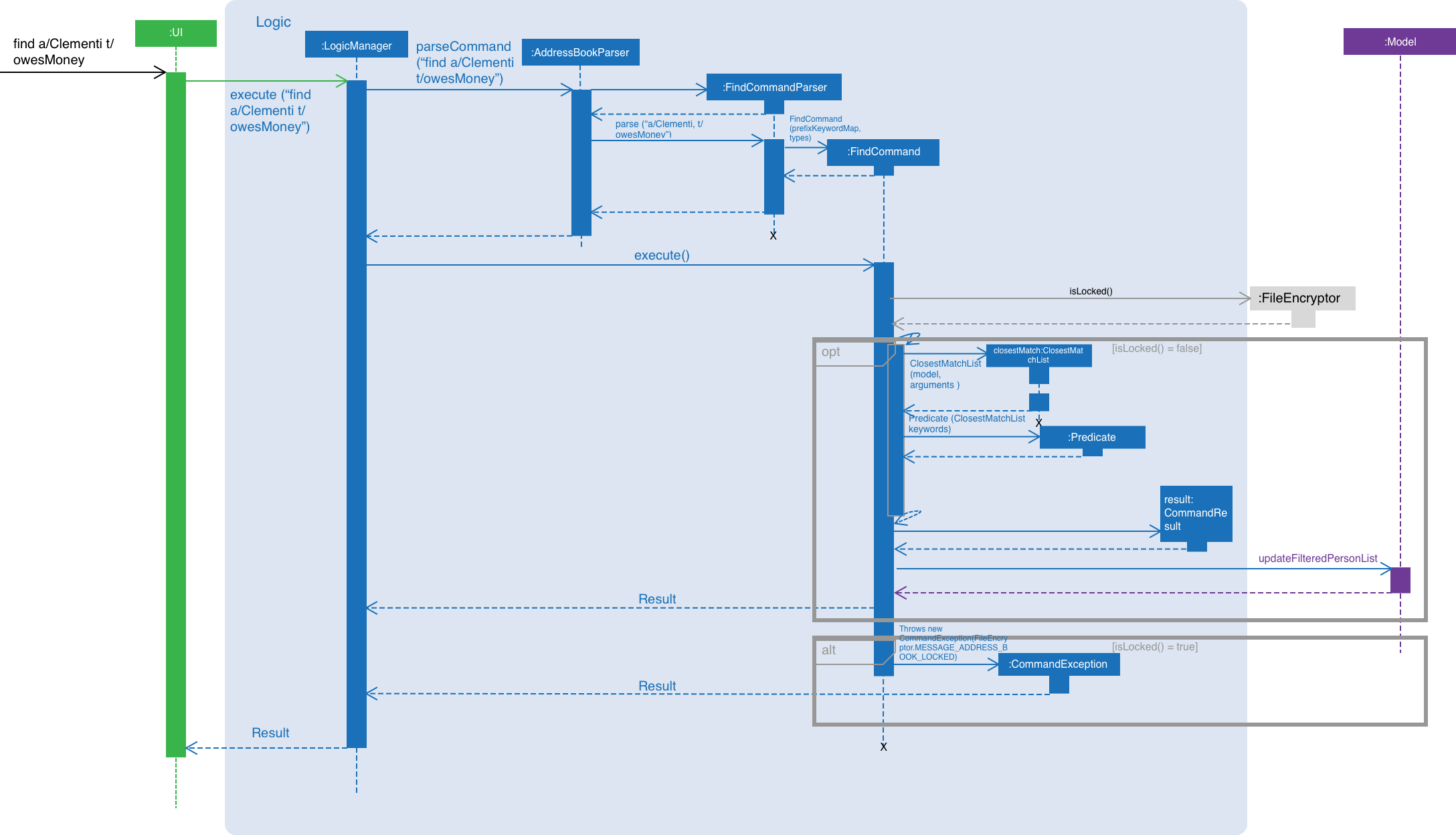
Figure 1. Interactions inside the logic component for the find a/Clementi t/owesMoney command.
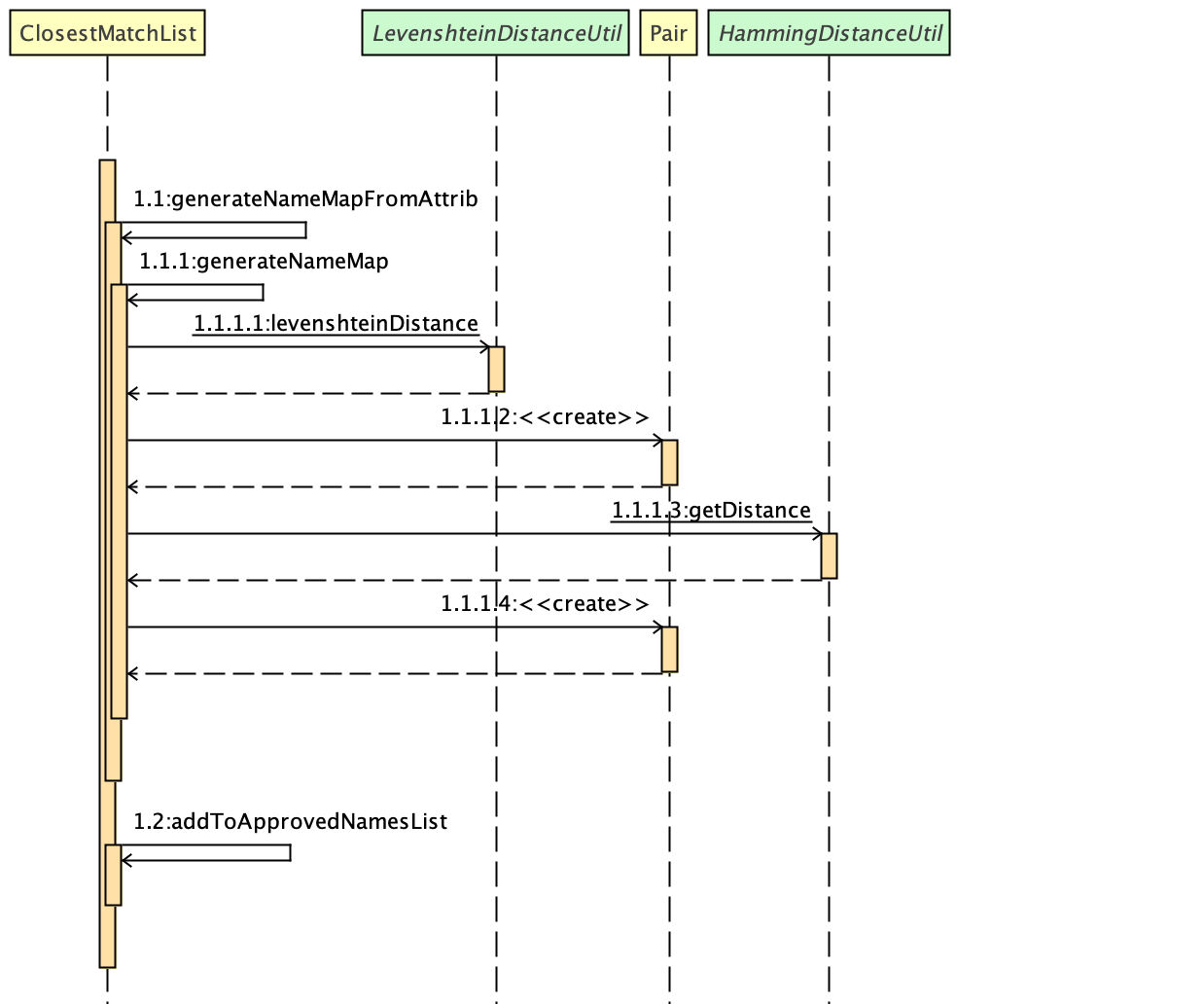
Figure 2. Interactions inside the ClosestMatchList class
3.10. Schedule
3.10.1. Current implementation
Updating the Schedule is facilitated by the ScheduleCommand class which extends the Command class.
ScheduleAddCommand, ScheduleEditCommand and ScheduleDeleteCommand further extends ScheduleCommand to add, edit and
delete entries in the Schedule respectively.
Activity
Each entry in the Schedule is an Activity. It consists of a String which takes the name of the activity
and the Date, of which the activity is due.
Schedule
Schedule is implemented with a TreeMap. It has the Date of activities as its key and a list of activities, which is due on the same
date, as its value.
Additionally, it implements the following main operations:
-
Schedule#add(Activity activity)— Add anActivitytoschedule. -
Schedule#delete(Activity activity)— Deletes anActivityfromschedule. -
Schedule#update(Activity target, Activity editedActivity)— Updates/edits anActivityin theschedule.targetis the activity to be edited.editedActivityis the new, changed, activity. -
Schedule#setSchedule(List<Activity> activities)— Setsschedulefrom alistof activities. This operation is executed when importing data from anXMLfile. This happens when you first start CorpPro. -
Schedule#getSchedule()— Returns the schedule with activities sorted byDateto be displayed in the GUI bySchedulePanelin theUIcomponent.
The schedule is instantiated in the AddressBook and have the main operations exposed in the Model interface as follows:
-
Model#addActivity(Activity activity)— ExposesSchedule#add(Activity activity). -
Model#deleteActivity(Activity activity)— ExposesSchedule#delete(Activity activity). -
Model#updateActivity(Activity target, Activity editedActivity)— ExposesSchedule#update(Activity target, Activity editedActivity). -
Model#getSchedule()— ExposesSchedule#getSchedule().
Storage
In addition to the CRUD (create, read, update and delete) functions, the schedule is also saved to an XML file
whenever you update it. This is facilitated by XmlAdaptedActivity which stores an Activity in an XML format.
XmlSerializableAddressBook then appends each XmlAdaptedActivity into a list and is saved in addressbook.xml.
Usage scenarios
Given below are examples of usage scenarios of how the schedule behaves when you carry out schedule commands.
Adding an activity:
Step 1. The user executes schedule-add d/01/01/2018 a/Complete report. to add an activity to their schedule.
Step 2. The user input is first parsed by AddressBookParser which creates a new ScheduleAddCommandParser object.
Step 3. The arguments, d/01/01/2018 a/Complete report., are then parsed by ScheduleAddCommandParser.
Step 4. ScheduleAddCommandParser checks the validity of the date and activity as input by the user. It then creates an
Activity object.
If the date or the activity name is not valid, an error would be returned to the user instead of creating an Activity object.
|
Step 5. ScheduleAddCommandParser then creates a new ScheduleAddCommand with the activity as its argument.
Step 6. ScheduleAddCommand is executed and calls Model#addActivity(activity) which creates the activity in the schedule.
Before calling Model#addActivity(activity), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
Step 7. indicateAddressBookChanged() is called within Model#addActivity(activity) to raise an AddressBookChangedEvent, that the information within the
address book is changed.
Step 8. The UI object, schedulePanel which is subscribed to the event, receives this updated information and updates
the display to show the correct information to the user.
The following sequence diagrams shows you how the add operation works:
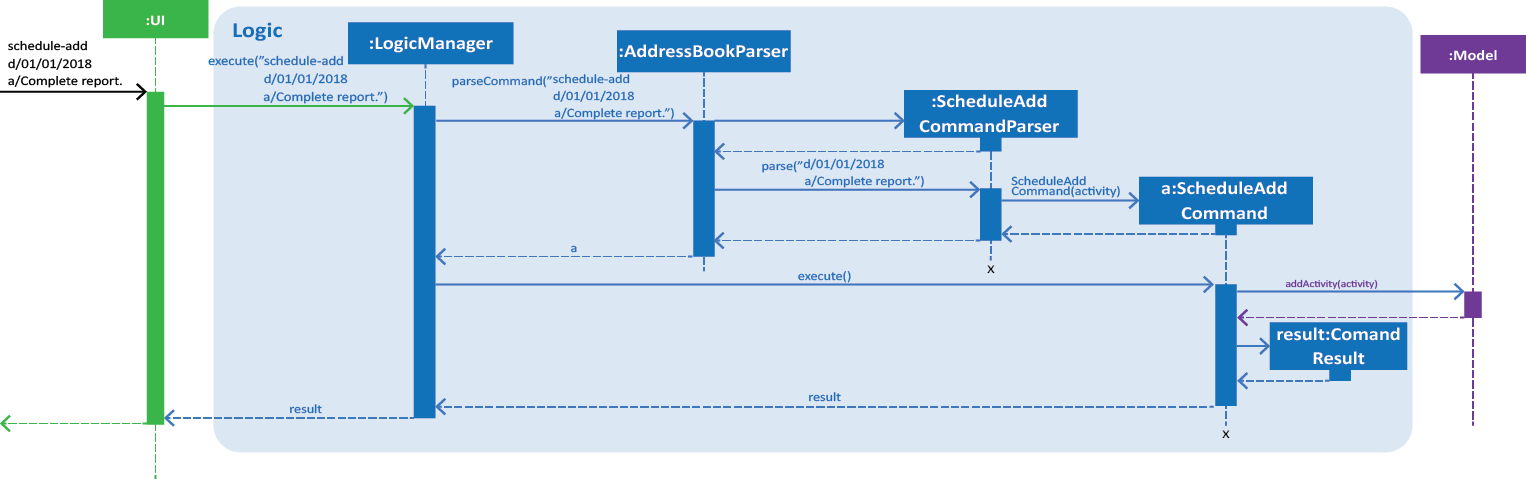
Figure 1. Interactions inside the Logic component for the schedule-add d/01/01/2018 a/Complete report. command.
|
The figure above illustrates the sequence from Step 1. to Step 5. |
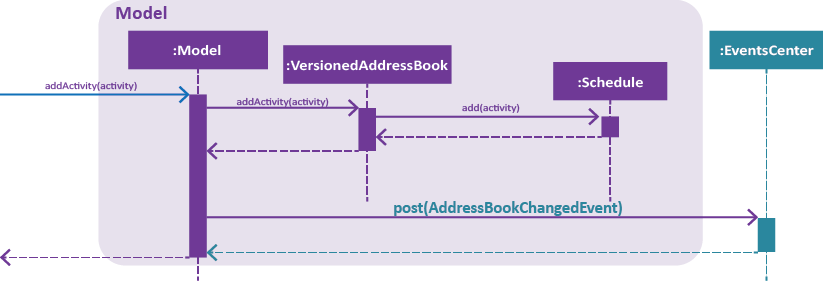
Figure 2. Interactions inside the Storage component for the schedule-add d/01/01/2018 a/Complete report. command.
|
The figure above illustrates the sequence of Step 6. and Step 7. |
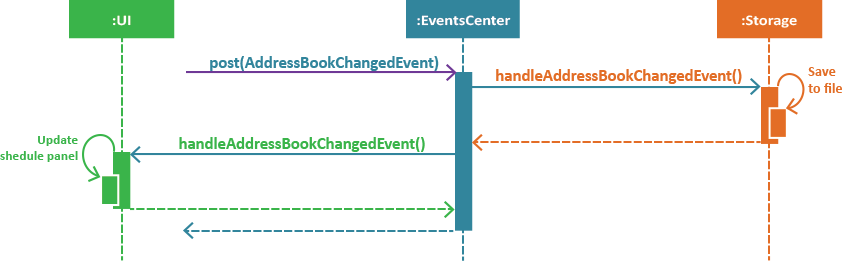
Figure 3. Interactions between the EventCenter, UI and Storage components for the schedule-add d/01/01/2018 a/Complete report. command.
|
The figure above illustrates the sequence of Step 8. |
Storage of each activity is facilitated by XmlAdaptedActivity which stores an Activity in an XML format. XmlSerializableAddressBook then appends each XmlAdaptedActivity into a list and is saved in addressbook.xml.
|
Editing an activity:
Step 1. The user executes schedule-edit 2 a/Interview intern. to edit an activity at INDEX 2 in their schedule.
Step 2. The user input is first parsed by AddressBookParser which creates a new ScheduleEditCommandParser object.
Step 3. The arguments, 2 a/Interview intern., are then parsed by ScheduleEditCommandParser.
Step 4. ScheduleEditCommandParser checks the validity of the index and activity as input by the user.
| If the activity name or index is not valid, an error would be returned to the user instead of editing an activity. |
Step 5. ScheduleEditCommandParser then creates a new ScheduleEditCommand with the INDEX and the new activity
String as its argument.
Step 6. ScheduleEditCommand gets target, the activity to be edited, via ScheduleCommand#getActivityFromIndex(model, index) and creates editedActivity, the new activity.
It then calls Model#updateActivity(target, editedActivity).
| If the index is not valid, i.e. out of range of the displayed schedule, an error would be returned to the user instead of editing an activity. |
Before calling Model#updateActivity(target, editedActivity), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
Step 7. Model#updateActivity(target, editedActivity) updates the corresponding activity in the schedule.
indicateAddressBookChanged() is called within Model#updateActivity(target, editedActivity) to raise an AddressBookChangedEvent that the information within the
address book is changed.
Step 8. The UI object, schedulePanel which is subscribed to the event, receives this updated information and
updates the display to show the correct information to the user.
The following sequence diagrams shows how the edit operation works:
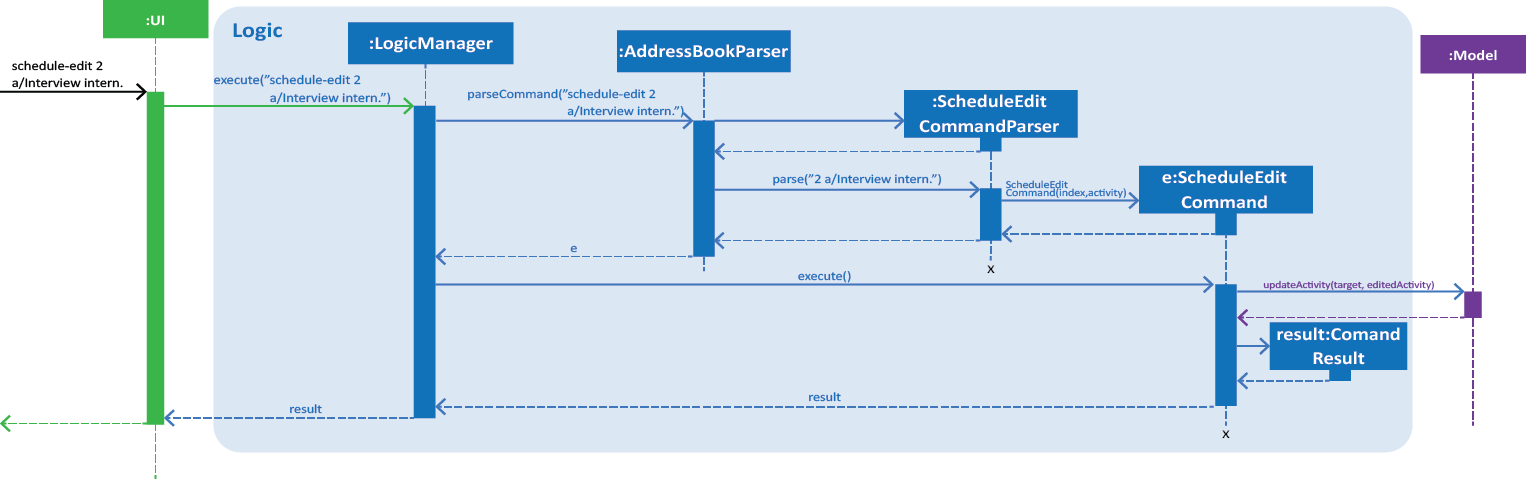
Figure 4. Interactions inside the Logic component for the schedule-edit 2 a/Interview intern. command.
|
The figure above illustrates the sequence from Step 1. to Step 6. |
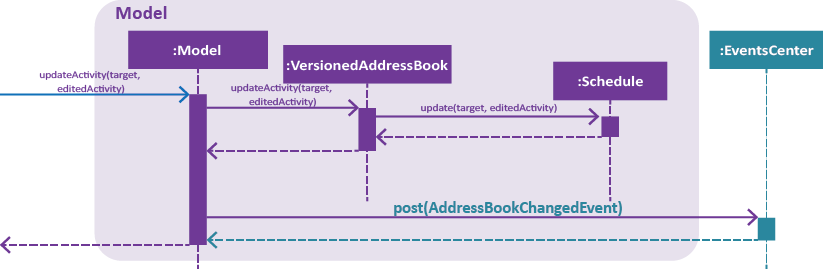
Figure 5. Interactions inside the Model component for the schedule-edit 2 a/Interview intern. command.
|
The figure above illustrates the sequence of Step 7. |
The interactions between the EventCenter, UI and Storage components for editing an activity (Step 8.) are similar to adding an activity (see Figure 3.).
Deleting an activity:
Step 1. The user executes schedule-delete 2 to delete the activity at INDEX 2 in their schedule.
Step 2. The user input is first parsed by AddressBookParser which creates a new ScheduleDeleteCommandParser object.
Step 3. ScheduleDeleteCommandParser checks the validity of the index as input by the user.
Step 4. ScheduleDeleteCommandParser then creates a new ScheduleDeleteCommand with the INDEX as its argument.
Step 5. ScheduleDeleteCommand gets the activity, to be deleted, via ScheduleCommand#getActivityFromIndex(model, index) and calls
Model#deleteActivity(activity).
| If the index is not valid, i.e. out of range of the displayed schedule, an error would be returned to the user instead of deleting an activity. |
Before calling Model#deleteActivity(activity), the address book is checked if it is encrypted with a password, via FileEncryptor.
It the address book is locked, an error would be displayed to the user instead of carrying on with the command.
|
Step 6. Model#deleteActivity(activity) deletes the corresponding activity from the schedule. indicateAddressBookChanged() is called
within Model#deleteActivity(activity) to raise an AddressBookChangedEvent, that the information within the
address book is changed.
Step 7. The UI object, schedulePanel which is subscribed to the event, receives this updated information and updates
the display to show the correct information to the user.
The sequence of deleting an activity is similar to editing an activity. Instead of updating the activity , it is deleted (see Figure 4. and Figure 5.).
The interactions between the EventCenter, UI and Storage components for deleting an activity (Step 7.) are similar to adding an activity (see Figure 3.).
3.10.2. Design Considerations
Aspect: Data structure of Schedule
-
Alternative 1:
Listof Activities-
Pros: Easy to implement.
-
Cons: Need to sort each activity by its date whenever the schedule is updated.
-
Cons: Larger time complexity.
-
-
Alternative 2 (Current choice):
TreeMapof Activities-
Pros: Activities are automatically sorted by their dates whenever the schedule is updated.
-
Pros: Faster time complexity.
-
Cons: Harder to implement.
-
Cons: Larger space complexity.
-
Aspect: Date of Activity
-
Alternative 1:
Stringof date in DD/MM/YYYY format-
Pros: Easy to implement and do not need to parse user input.
-
Cons: Need to implement comparators to sort the dates of activity.
-
Cons: Not flexible. Unable to include and sort by time in future implementations.
-
-
Alternative 2 (Current choice): Usage of
java.util.Date-
Pros: Easy to implement.
-
Pros: Able to sort by time in future implementations.
-
Cons: Need to parse
Datewhen converting it toString. -
Cons: Need to parse user inputs to convert
StringtoDate.
-
4. Documentation
We use asciidoc for writing documentation.
| We chose asciidoc over Markdown because asciidoc, although a bit more complex than Markdown, provides more flexibility in formatting. |
4.1. Editing Documentation
See UsingGradle.adoc to learn how to render .adoc files locally to preview the end result of your edits.
Alternatively, you can download the AsciiDoc plugin for IntelliJ, which allows you to preview the changes you have made to your .adoc files in real-time.
4.2. Publishing Documentation
See UsingTravis.adoc to learn how to deploy GitHub Pages using Travis.
4.3. Converting Documentation to PDF format
We use Google Chrome for converting documentation to PDF format, as Chrome’s PDF engine preserves hyperlinks used in webpages.
Here are the steps to convert the project documentation files to PDF format.
-
Follow the instructions in UsingGradle.adoc to convert the AsciiDoc files in the
docs/directory to HTML format. -
Go to your generated HTML files in the
build/docsfolder, right click on them and selectOpen with→Google Chrome. -
Within Chrome, click on the
Printoption in Chrome’s menu. -
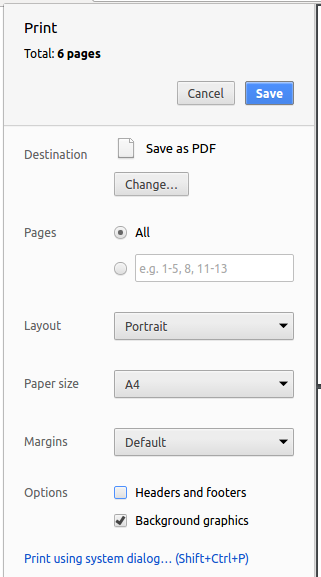
Set the destination to
Save as PDF, then clickSaveto save a copy of the file in PDF format. For best results, use the settings indicated in the screenshot below.
4.4. Site-wide Documentation Settings
The build.gradle file specifies some project-specific asciidoc attributes which affects how all documentation files within this project are rendered.
Attributes left unset in the build.gradle file will use their default value, if any.
|
| Attribute name | Description | Default value |
|---|---|---|
|
The name of the website. If set, the name will be displayed near the top of the page. |
not set |
|
URL to the site’s repository on GitHub. Setting this will add a "View on GitHub" link in the navigation bar. |
not set |
|
Define this attribute if the project is an official SE-EDU project. This will render the SE-EDU navigation bar at the top of the page, and add some SE-EDU-specific navigation items. |
not set |
4.5. Per-file Documentation Settings
Each .adoc file may also specify some file-specific asciidoc attributes which affects how the file is rendered.
Asciidoctor’s built-in attributes may be specified and used as well.
Attributes left unset in .adoc files will use their default value, if any.
|
| Attribute name | Description | Default value |
|---|---|---|
|
Site section that the document belongs to.
This will cause the associated item in the navigation bar to be highlighted.
One of: * Official SE-EDU projects only |
not set |
|
Set this attribute to remove the site navigation bar. |
not set |
4.6. Site Template
The files in docs/stylesheets are the CSS stylesheets of the site.
You can modify them to change some properties of the site’s design.
The files in docs/templates controls the rendering of .adoc files into HTML5.
These template files are written in a mixture of Ruby and Slim.
|
Modifying the template files in |
5. Testing
5.1. Running Tests
There are three ways to run tests.
| The most reliable way to run tests is the 3rd one. The first two methods might fail some GUI tests due to platform/resolution-specific idiosyncrasies. |
Method 1: Using IntelliJ JUnit test runner
-
To run all tests, right-click on the
src/test/javafolder and chooseRun 'All Tests' -
To run a subset of tests, you can right-click on a test package, test class, or a test and choose
Run 'ABC'
Method 2: Using Gradle
-
Open a console and run the command
gradlew clean allTests(Mac/Linux:./gradlew clean allTests)
| See UsingGradle.adoc for more info on how to run tests using Gradle. |
Method 3: Using Gradle (headless)
Thanks to the TestFX library we use, our GUI tests can be run in the headless mode. In the headless mode, GUI tests do not show up on the screen. That means the developer can do other things on the Computer while the tests are running.
To run tests in headless mode, open a console and run the command gradlew clean headless allTests (Mac/Linux: ./gradlew clean headless allTests)
5.2. Types of tests
We have two types of tests:
-
GUI Tests - These are tests involving the GUI. They include,
-
System Tests that test the entire App by simulating user actions on the GUI. These are in the
systemtestspackage. -
Unit tests that test the individual components. These are in
seedu.address.uipackage.
-
-
Non-GUI Tests - These are tests not involving the GUI. They include,
-
Unit tests targeting the lowest level methods/classes.
e.g.seedu.address.commons.StringUtilTest -
Integration tests that are checking the integration of multiple code units (those code units are assumed to be working).
e.g.seedu.address.storage.StorageManagerTest -
Hybrids of unit and integration tests. These test are checking multiple code units as well as how the are connected together.
e.g.seedu.address.logic.LogicManagerTest
-
5.3. Troubleshooting Testing
Problem: HelpWindowTest fails with a NullPointerException.
-
Reason: One of its dependencies,
HelpWindow.htmlinsrc/main/resources/docsis missing. -
Solution: Execute Gradle task
processResources.
6. Dev Ops
6.1. Build Automation
See UsingGradle.adoc to learn how to use Gradle for build automation.
6.2. Continuous Integration
We use Travis CI and AppVeyor to perform Continuous Integration on our projects. See UsingTravis.adoc and UsingAppVeyor.adoc for more details.
6.3. Coverage Reporting
We use Coveralls to track the code coverage of our projects. See UsingCoveralls.adoc for more details.
6.4. Documentation Previews
When a pull request has changes to asciidoc files, you can use Netlify to see a preview of how the HTML version of those asciidoc files will look like when the pull request is merged. See UsingNetlify.adoc for more details.
6.5. Making a Release
Here are the steps to create a new release.
-
Update the version number in
MainApp.java. -
Generate a JAR file using Gradle.
-
Tag the repo with the version number. e.g.
v0.1 -
Create a new release using GitHub and upload the JAR file you created.
6.6. Managing Dependencies
A project often depends on third-party libraries. For example, Address Book depends on the Jackson library for XML parsing. Managing these dependencies can be automated using Gradle. For example, Gradle can download the dependencies automatically, which is better than these alternatives.
a. Include those libraries in the repo (this bloats the repo size)
b. Require developers to download those libraries manually (this creates extra work for developers)
Appendix A: Text Prediction low level details
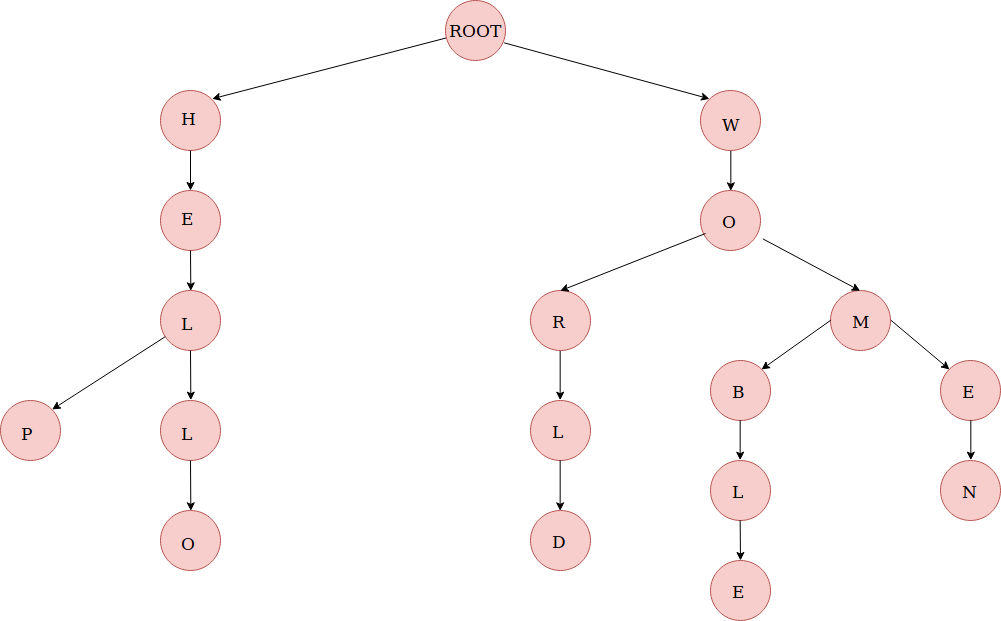
The low level implementation of text prediction is done in Trie. The internal data structure is a Tree structure where each character is stored as a node and strings built into a single tree.
A node has a endNode flag that determines if that node represents the last character of the predicted string value. If such a node is reached, the entire string value is appended to the prediction list.
The data structure can be visualised in the diagram below:
In addition, Trie implements the following main operations:
-
Trie#insert(String value)— inserts a string into the data structure. -
Trie#remove(String value)— removes a string from the data structure. -
Trie#getPredictList(String prefix)— retrieve a list of predicted string values that completes the prefix.
The prediction implementation is achieved by utilising depth first search (DFS) algorithm in the data structure, starting from the node representing the last character of the prefix.
The prediction algorithm is illustrated with the help of the following diagram:
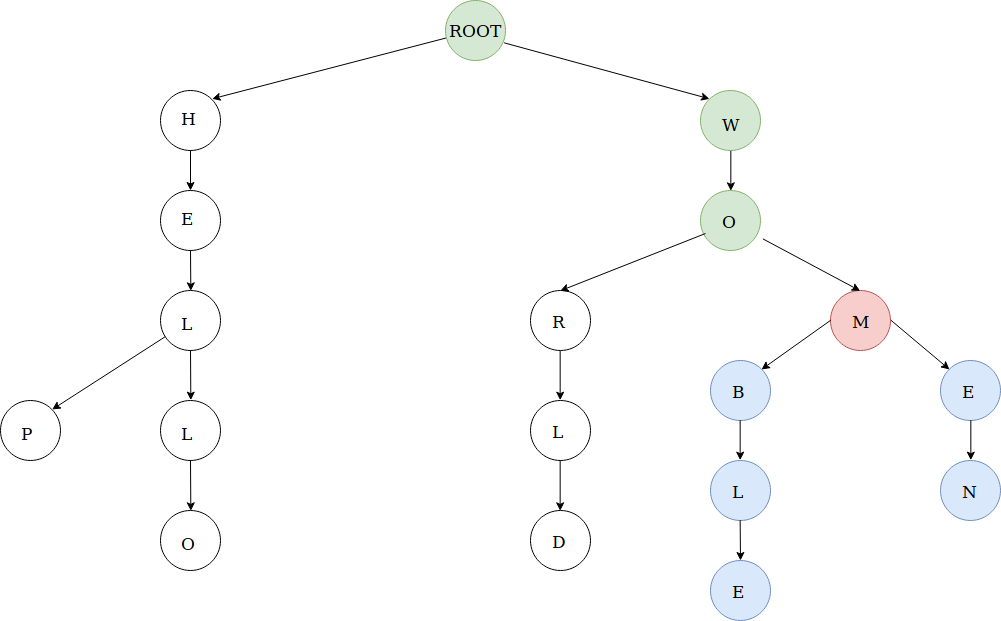
For example, we call the method getPredictList("wom").
The algorithm works by first traversing the route (green circles) that represents "wom" and stopping at the m node (red circle). The algorithm proceeds to DFS from that node and explore all it’s children nodes (blue circles).
Hence, calling getPredictList("wom") will return a list containing the elements:
-
"en" -
"ble"
Appendix B: Suggested Programming Tasks to Get Started
Suggested path for new programmers:
-
First, add small local-impact (i.e. the impact of the change does not go beyond the component) enhancements to one component at a time. Some suggestions are given in Section B.1, “Improving each component”.
-
Next, add a feature that touches multiple components to learn how to implement an end-to-end feature across all components. Section B.2, “Creating a new command:
remark” explains how to go about adding such a feature.
B.1. Improving each component
Each individual exercise in this section is component-based (i.e. you would not need to modify the other components to get it to work).
Logic component
Scenario: You are in charge of logic. During dog-fooding, your team realize that it is troublesome for the user to type the whole command in order to execute a command. Your team devise some strategies to help cut down the amount of typing necessary, and one of the suggestions was to implement aliases for the command words. Your job is to implement such aliases.
Do take a look at Section 2.3, “Logic component” before attempting to modify the Logic component.
|
-
Add a shorthand equivalent alias for each of the individual commands. For example, besides typing
clear, the user can also typecto remove all persons in the list.
Model component
Scenario: You are in charge of model. One day, the logic-in-charge approaches you for help. He wants to implement a command such that the user is able to remove a particular tag from everyone in the address book, but the model API does not support such a functionality at the moment. Your job is to implement an API method, so that your teammate can use your API to implement his command.
Do take a look at Section 2.4, “Model component” before attempting to modify the Model component.
|
-
Add a
removeTag(Tag)method. The specified tag will be removed from everyone in the address book.
Ui component
Scenario: You are in charge of ui. During a beta testing session, your team is observing how the users use your address book application. You realize that one of the users occasionally tries to delete non-existent tags from a contact, because the tags all look the same visually, and the user got confused. Another user made a typing mistake in his command, but did not realize he had done so because the error message wasn’t prominent enough. A third user keeps scrolling down the list, because he keeps forgetting the index of the last person in the list. Your job is to implement improvements to the UI to solve all these problems.
Do take a look at Section 2.2, “UI component” before attempting to modify the UI component.
|
-
Use different colors for different tags inside person cards. For example,
friendstags can be all in brown, andcolleaguestags can be all in yellow.Before
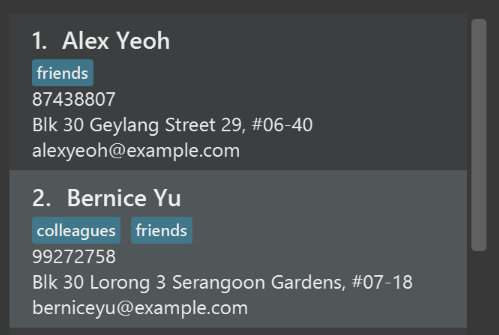
After
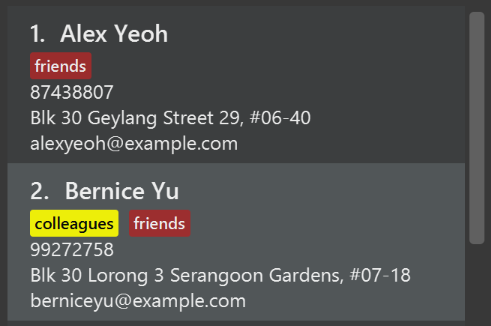
-
Modify
NewResultAvailableEventsuch thatResultDisplaycan show a different style on error (currently it shows the same regardless of errors).Before
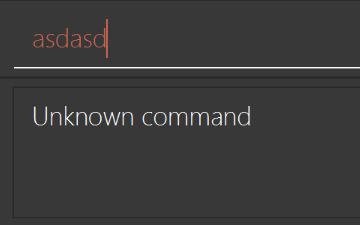
After
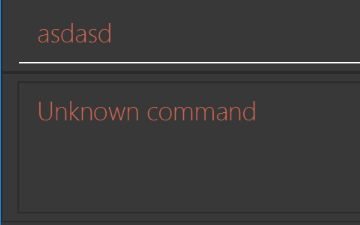
-
Modify the
StatusBarFooterto show the total number of people in the address book.Before
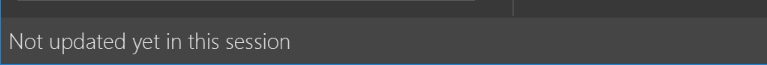
After
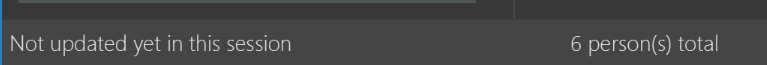
Storage component
Scenario: You are in charge of storage. For your next project milestone, your team plans to implement a new feature of saving the address book to the cloud. However, the current implementation of the application constantly saves the address book after the execution of each command, which is not ideal if the user is working on limited internet connection. Your team decided that the application should instead save the changes to a temporary local backup file first, and only upload to the cloud after the user closes the application. Your job is to implement a backup API for the address book storage.
Do take a look at Section 2.5, “Storage component” before attempting to modify the Storage component.
|
-
Add a new method
backupAddressBook(ReadOnlyAddressBook), so that the address book can be saved in a fixed temporary location.
B.2. Creating a new command: remark
By creating this command, you will get a chance to learn how to implement a feature end-to-end, touching all major components of the app.
Scenario: You are a software maintainer for addressbook, as the former developer team has moved on to new projects. The current users of your application have a list of new feature requests that they hope the software will eventually have. The most popular request is to allow adding additional comments/notes about a particular contact, by providing a flexible remark field for each contact, rather than relying on tags alone. After designing the specification for the remark command, you are convinced that this feature is worth implementing. Your job is to implement the remark command.
B.2.1. Description
Edits the remark for a person specified in the INDEX.
Format: remark INDEX r/[REMARK]
Examples:
-
remark 1 r/Likes to drink coffee.
Edits the remark for the first person toLikes to drink coffee. -
remark 1 r/
Removes the remark for the first person.
B.2.2. Step-by-step Instructions
[Step 1] Logic: Teach the app to accept 'remark' which does nothing
Let’s start by teaching the application how to parse a remark command. We will add the logic of remark later.
Main:
-
Add a
RemarkCommandthat extendsCommand. Upon execution, it should just throw anException. -
Modify
AddressBookParserto accept aRemarkCommand.
Tests:
-
Add
RemarkCommandTestthat tests thatexecute()throws an Exception. -
Add new test method to
AddressBookParserTest, which tests that typing "remark" returns an instance ofRemarkCommand.
[Step 2] Logic: Teach the app to accept 'remark' arguments
Let’s teach the application to parse arguments that our remark command will accept. E.g. 1 r/Likes to drink coffee.
Main:
-
Modify
RemarkCommandto take in anIndexandStringand print those two parameters as the error message. -
Add
RemarkCommandParserthat knows how to parse two arguments, one index and one with prefix 'r/'. -
Modify
AddressBookParserto use the newly implementedRemarkCommandParser.
Tests:
-
Modify
RemarkCommandTestto test theRemarkCommand#equals()method. -
Add
RemarkCommandParserTestthat tests different boundary values forRemarkCommandParser. -
Modify
AddressBookParserTestto test that the correct command is generated according to the user input.
[Step 3] Ui: Add a placeholder for remark in PersonCard
Let’s add a placeholder on all our PersonCard s to display a remark for each person later.
Main:
-
Add a
Labelwith any random text insidePersonListCard.fxml. -
Add FXML annotation in
PersonCardto tie the variable to the actual label.
Tests:
-
Modify
PersonCardHandleso that future tests can read the contents of the remark label.
[Step 4] Model: Add Remark class
We have to properly encapsulate the remark in our Person class. Instead of just using a String, let’s follow the conventional class structure that the codebase already uses by adding a Remark class.
Main:
-
Add
Remarkto model component (you can copy fromAddress, remove the regex and change the names accordingly). -
Modify
RemarkCommandto now take in aRemarkinstead of aString.
Tests:
-
Add test for
Remark, to test theRemark#equals()method.
[Step 5] Model: Modify Person to support a Remark field
Now we have the Remark class, we need to actually use it inside Person.
Main:
-
Add
getRemark()inPerson. -
You may assume that the user will not be able to use the
addandeditcommands to modify the remarks field (i.e. the person will be created without a remark). -
Modify
SampleDataUtilto add remarks for the sample data (delete youraddressBook.xmlso that the application will load the sample data when you launch it.)
[Step 6] Storage: Add Remark field to XmlAdaptedPerson class
We now have Remark s for Person s, but they will be gone when we exit the application. Let’s modify XmlAdaptedPerson to include a Remark field so that it will be saved.
Main:
-
Add a new Xml field for
Remark.
Tests:
-
Fix
invalidAndValidPersonAddressBook.xml,typicalPersonsAddressBook.xml,validAddressBook.xmletc., such that the XML tests will not fail due to a missing<remark>element.
[Step 6b] Test: Add withRemark() for PersonBuilder
Since Person can now have a Remark, we should add a helper method to PersonBuilder, so that users are able to create remarks when building a Person.
Tests:
-
Add a new method
withRemark()forPersonBuilder. This method will create a newRemarkfor the person that it is currently building. -
Try and use the method on any sample
PersoninTypicalPersons.
[Step 7] Ui: Connect Remark field to PersonCard
Our remark label in PersonCard is still a placeholder. Let’s bring it to life by binding it with the actual remark field.
Main:
-
Modify
PersonCard's constructor to bind theRemarkfield to thePerson's remark.
Tests:
-
Modify
GuiTestAssert#assertCardDisplaysPerson(…)so that it will compare the now-functioning remark label.
[Step 8] Logic: Implement RemarkCommand#execute() logic
We now have everything set up… but we still can’t modify the remarks. Let’s finish it up by adding in actual logic for our remark command.
Main:
-
Replace the logic in
RemarkCommand#execute()(that currently just throws anException), with the actual logic to modify the remarks of a person.
Tests:
-
Update
RemarkCommandTestto test that theexecute()logic works.
B.2.3. Full Solution
See this PR for the step-by-step solution.
Appendix C: Product Scope
Target user profile:
-
has a need to manage a significant number of contacts
-
prefer desktop apps over other types
-
can type fast
-
prefers typing over mouse input
-
is reasonably comfortable using CLI apps
Value proposition: manage contacts faster than a typical mouse/GUI driven app
Appendix D: User Stories
Priorities: High (must have) - * * *, Medium (nice to have) - * *, Low (unlikely to have) - *
Functional Requirements:
| Priority | As a … | I want to … | So that I can… |
|---|---|---|---|
|
new user |
see usage instructions |
refer to instructions when I forget how to use the App |
|
user |
add a new person |
|
|
user |
delete a person |
remove entries that I no longer need |
|
user |
find a person by name |
locate details of persons without having to go through the entire list |
|
user who values time |
autocomplete my commands |
execute commands faster. |
|
forgetful user |
approximate my search input |
get the closest output suggestions I need. |
|
employee |
access the full profile of my clients |
retrieve their information when required. |
|
organized user |
create groups |
mass contact easily. |
|
meticulous supervisor |
access my team’s profiles easily |
I can keep track of each member conveniently. |
|
overworked employee |
i need a backup file |
information is not immediately lost when i accidentally delete contacts. |
|
user |
hide private contact details by default |
minimize chance of someone else seeing them by accident |
|
organised user |
can sort my contacts based on rank/position |
respond to them appropriately. |
|
efficient user |
send mass emails with a single command |
email large groups quickly. |
|
meticulous employee |
add notes along with my contacts |
keep track of my working relations |
|
supervisor |
access my subordinate’s Key-Performance-Index |
keep track of their work quality. |
|
user with many persons in the address book |
sort persons by name |
locate a person easily |
|
user |
schedule tasks in a calendar |
notified of my appointments. |
|
user |
schedule tasks in a calendar |
notified of when tasks are due. |
|
forgetful user |
look at the photos of my contacts |
recognise the person. |
Appendix E: Use Cases
(For all use cases below, the System is the AddressBook and the Actor is the user, unless specified otherwise)
Use case: Viewing help
MSS
-
User requests a list of commands
-
AddressBook shows a list of commands
Use case ends.
Use case: Add person
MSS 1. User requests to Add a person with the relevant details. 2. AddressBook adds the person into the list and shows a success message.
+ Use case ends.
Extensions
-
1a. Given details are invalid.
-
1a1. AddressBook shows an error message.
Use case resumes at step 1.
-
Use case: List persons
MSS
-
User requests to list persons
-
AddressBook shows a list of persons
Use case ends.
Extensions
-
2a. The list is empty.
Use case ends.
Use case: Find persons
MSS
-
User requests to search by address
-
Address book shows a list of persons living under that address
-
User requests to search for a specific tag and the previous address
-
Address book refines the search results by displaying people who live in the specified address and is tagged
Use case ends.
Extensions
-
2a. No similar keywords within the address book.
-
2a1. Address book shows list of persons with similar keywords to the one originally searched.
Use case resumes at step 3.
-
Use case: Delete person
MSS
-
User requests to list persons
-
AddressBook shows a list of persons
-
User requests to delete a specific person in the list
-
AddressBook deletes the person
Use case ends.
Extensions
-
2a. The list is empty.
Use case ends.
-
3a. The given index is invalid.
-
3a1. AddressBook shows an error message.
Use case resumes at step 2.
-
Use case: Back Up data
MSS
-
User requests to back up data
-
AddressBook shows that data has been backed up
Use case ends.
Use case: Restore data
MSS
-
User requests to list snapshots of all backups
-
AddressBook shows a list of snapshots
-
User requests to restore a specific snapshot in the list
-
AddressBook is restored to the time and date of the restored backup.
Use case ends.
Extensions
-
2a. The list is empty.
Use case ends.
-
3a. The given index is invalid.
-
3a1. AddressBook shows an error message.
Use case resumes at step 2.
-
Use case: Export data to a directory
MSS
-
User requests to export the data to the directory
-
AddressBook shows that the file has been exported
Use case ends.
Extensions
-
2a. Directory does not exist
-
2a1. AddressBook shows an error message.
Use case ends.
-
Use case: Import data from a directory
MSS
-
User requests to import the data from a directory
-
AddressBook shows that the file has been imported
-
AddressBook will include the imported data.
Use case ends.
Extensions
-
2a. Directory does not exist
-
2a1. AddressBook shows an error message.
Use case ends.
-
Use case: Lock address book
MSS
-
User requests to encrypt addressbook with password
-
Address book shows encrypted message
Use case ends.
Extensions
-
1a. Address book is already encrypted.
-
1a1. Address book will decrypt the data instead with the given password.
Use case ends.
-
Use case: Unlock address book
MSS
-
User requests to decrypt address book with password
-
Address book shows decrypted message
Use case ends.
Extensions
-
1a. Address book is already decrypted.
-
1a1. Address book will encrypt the data instead with the given password.
-
-
1b. Incorrect password entered.
-
1b1. Address book will display incorrect password message.
Use case ends.
-
Use case: Text prediction
MSS
-
User input some characters.
-
User requests text prediction with
Tab. -
Address book auto completes user input with closest prediction.
Use case ends.
Extensions
-
2a. There is more than one prediction.
-
2a1. Address book lists multiple predictions.
-
2a2. Use case resumes from step 1.
-
Use case: Send email
MSS
-
User requests to send email with mail command.
-
Address book opens email application with appropriate recipients.
Use case ends.
Extensions
-
1a. Input command has invalid format.
-
1a1. Address book displays format error.
Use case ends.
-
Use case: Add an activity to the schedule
MSS
-
User requests to add an activity to the schedule.
-
Address book adds the activity to the schedule
Use case ends.
Extensions
-
1a. Input command has invalid format.
-
1a1. Address book displays format error.
Use case ends.
-
E.1. Use case: Edit an activity in the schedule
MSS
-
User requests to edit an activity in the schedule.
-
Address book edits the activity in the schedule
Use case ends.
Extensions
-
1a. Input command has invalid format.
-
1a1. Address book displays format error.
Use case ends.
-
E.2. Use case: Delete an activity from the schedule
MSS
-
User requests to delete an activity from the schedule.
-
Address book delete the activity from the schedule
Use case ends.
Extensions
-
1a. Input command has invalid format.
-
1a1. Address book displays format error.
Use case ends.
-
Appendix F: Non Functional Requirements
-
Should work on any mainstream OS as long as it has Java
9or higher installed. -
Should be able to hold up to 1000 persons without a noticeable sluggishness in performance for typical usage.
-
A user with above average typing speed for regular English text (i.e. not code, not system admin commands) should be able to accomplish most of the tasks faster using commands than using the mouse.
-
A busy employee should be able to get back to work quickly using an intuitive interface to get information from the address book fast.
-
A secretary should be able to refer and contact different people with accurate information.
-
A busy employee should be able to get back to work fast by having quick access to information required.
-
Should have a way to keep information confidential and safe from any unauthenticated personnel.
-
Should be able to transfer information between machines easily by making the address book small and compact
Appendix H: Instructions for Manual Testing
Given below are instructions to test the app manually.
| These instructions only provide a starting point for testers to work on; testers are expected to do more exploratory testing. |
H.1. Adding a person
Adding a person to the address book.
Prerequisites: Carry out the following commands sequentially:
-
Test case:
add n/Alexia Tok p/22224444 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: The person is added to the contact list. -
Test case:
add n/Alexia Tok p/22224444 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: No person is added as the person "Alexia Tok" is already in the contact list. Error details shown in the status message. -
Test case:
add n/Bob Teo p/23q e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: No person is added as the phone number is invalid. Error details shown in the status message. -
Test case:
add n/Bob Teo p/99008800 e/ATexamplecom a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: No person is added as the email is invalid. Error details shown in the status message. -
Test case:
add n/Bob Teo p/99008800 e/AT@example.com a/123, Potong Pasir, 1234665 r/… k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: No person is added as the position is invalid. Error details shown in the status message. -
Test case:
add n/Bob Teo p/99008800 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/6 d/AT is a good friend t/friend t/colleague 2
Expected: No person is added as the kpi is invalid. Error details shown in the status message. -
Test case:
add n/Bob Teo p/99008800 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/?#$% t/friend t/colleague 2
Expected: No person is added as the note is invalid. Error details shown in the status message. -
Test case:
add n/Bob Teo p/99008800 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 3
Expected: No person is added as the tag is invalid. Error details shown in the status message.
H.2. Editing a person
Editing a person in the address book.
Prerequisites: There are multiple persons in the contact list.
-
Test case:
edit 1 p/22224444 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2
Expected: The first person in the contact list is edited. -
Test case:
edit 0 p/12345678
Expected: No person is edited. Error details shown in status message. -
Test case:
edit all/ n/Hercules fatty
Expected: No persons is edited. Error details shown in status message.
H.3. Listing persons
Listing persons in the address book.
Prerequisites: There are multiple persons in the contact list.
-
Test case:
list
Expected: All contacts in the address book will be listed and shown in the contacts panel. -
Test case:
list t/colleagues
Expected: All contacts with the tagcolleagueswill be listed and shown. -
Test case:
list k/5.0
Expected: All contacts with KPI value of5.0will be listed and shown.
H.4. Selecting persons
Selecting persons in the address book.
Prerequisites: There are at least 7 persons in the contacts list.
-
Test case:
select 1
Expected: First contact will be highlighted in the contacts panel and information shown in information panel. -
Test case:
select 1 2 3
Expected: First three contacts will be highlighted. -
Test case:
select 1-3, 5-7
Expected: First three and 5th to 7th contacts will be highlighted.
H.5. Predicting text
Invoking text prediction in the address book.
Prerequisites: There are the sample contacts in the address book.
-
Test case:
fand press Tab.
Expected: The command box should automatically be filled to the command `find `. -
Test case: Continuing from previous test case, append with
n/Aland press Tab.
Expected: The command box should be automatically filled tofind n/Alex Yeoh. -
Other commands to try:
add,delete,password.
| Some arguments do not work since they are unsupported. Refer to Text Prediction in the User Guide for more details. |
H.6. Searching for a person
Finding a person in the address book.
Prerequisites: The following commands must be entered, "Alexia Tok" and "Marcus Tok" must exist within the contact list:
-
add n/Alexia Tok p/22224444 e/AT@example.com a/123, Potong Pasir, 1234665 r/Boss k/4.5 d/AT is a good friend t/friend t/colleague 2 -
add n/Marcus Tok p/12341234 e/MT@example.com a/123, Admiraly, 1234665 r/Cleaner k/4.0 d/MT is a bad cleaner t/notFriend t/colleague 2-
Test case:
find n/Tok
Expected: "Marcus Tok" and "Alexia Tok" will show up in the contacts panel. -
Test case:
find k/4.0
Expected: "Marcus Tok" will show up in the contacts panel. -
Test case:
find k/4
Expected: "Marcus Tok" and "Alexia Tok" will show up in the contacts panel. -
Test case:
find r/bass
Expected: "Alexia Tok" with position "Boss" will show up in the contacts panel.Keywords guessed: {Boss}will show at the status message as "bass" is a closer match to "Boss"
-
H.7. Locking and unlocking
Locking and unlocking of the address book.
Prerequisites: Address book should not be locked. Check path at ./data/addressbook.xml to ensure that it is not encrypted: addressbook.xml.encrypted and that addressbook.xml exists.
-
Test case:
password hello
Expected: A status message "File encrypted!" will be displayed to the user and the contacts panel will be cleared. All further commands at this point will show a message "Address book is locked, please key in password".Schedule panel will still be visible and not cleared. But the user will not be able to update it. Closing and re-opening the address book will clear it. -
Test case:
password test
Prerequisites: This test case should be carried out after the previous test case.
Expected: A status message "Password mismatch!" will be displayed to the user and the address book will remain locked. -
Test case:
password hello
Prerequisites: This test case should be carried out after the previous test case 1.
Expected: A status message "File decrypted!" will be displayed to the user, the contacts panel and schedule will be refreshed to show the data that was encrypted.
H.8. Deleting a person
Deleting a person while all persons are listed.
Prerequisites: List all persons using the list command. Multiple persons in the list.
-
Test case:
delete 1
Expected: First contact is deleted from the list. Details of the deleted contact shown in the status message. Timestamp in the status bar is updated. -
Test case:
delete 1 2 3
Expected: First three contacts will be deleted. -
Test case:
delete 1-3, 5-7
Expected: First three and 5th to 7th contacts will be deleted. -
Test case:
delete 0
Expected: No person is deleted. Error details shown in the status message. Status bar remains the same. -
Other incorrect delete commands to try:
delete,delete x(where x is larger than the list size)
Expected: Similar to previous.
H.9. Updating the Schedule
Updating activities in the schedule.
Prerequisites: Carry out the following commands sequentially:
-
Test case:
schedule-add d/30/10/2018 a/Attend meeting with Alex.
Expected: activity "Attend meeting with Alex." is added to the schedule. -
Test case:
schedule-add d/30/10/2018 a/Attend meeting with Alex.
Expected: another activity, "Attend meeting with Alex.", is added to the schedule. -
Test case:
schedule-edit 2 a/Attend meeting with Alexia.
Expected: The second activity is edited to "Attend meeting with Alexia.". -
Test case:
schedule-edit 0 a/Test bugs
Expected: No activity is edited. Error details shown in the status message. Schedule panel remains the same. -
Test case:
schedule-delete 1
Expected: First activity is deleted from the schedule. -
Test case:
schedule-delete 0
Expected: No activity is deleted. Error details shown in the status message.
H.10. Backing up and restoring data in the address book
Backing up and restoring data in the address book.
Prerequisites: Make a backup with the backup command.
-
Test case:
restore-snapshot
Expected: One snapshot will be shown on the screen if this is your first backup. If this is not your first backup, the list will be populated with older snapshots. -
Test case:
restore 0
Expected: No data restored. Error details shown in the status message. Status bar remains the same. -
Other incorrect restore commands to try:
restore,delete x(where x is larger than the list size)
Expected: Similar to previous.
H.11. Exporting data from the address book
Exporting data from the address book. Prerequisites: Make sure the address book is populated with people
-
Test case:
export
Expected: A copy of the contacts inCSVformat will be created in aexportsfolder in the root directory -
Test case:
export DIRECTORY FILENAME
Expected: A copy of the contacts inCSVformat will be created in the designated folder with the designated name. -
Any directory or file name that does not exist:
export FALSE_DIRECTORY FILENAME,export DIRECTORY FALSE_FILENAME.
Expected: Nothing will be created. An error will be thrown to the user. Status bar will remain the same.
H.12. Importing data to the address book
Importing data from the address book.
-
Test case:
import DIRECTORY FILENAME
Expected: A copy of the contacts inCSVformat will be created in the designated folder with the designated name. -
Test case:
import
Expected: Nothing will be created. An error will be thrown to the user. Status bar will remain the same. -
Any directory or file name that does not exist:
import FALSE_DIRECTORY FILENAME,import DIRECTORY FALSE_FILENAME.
Expected: Similar to previous